Active directory / LDAP
TrendMiner supports switching to Active Directory / LDAP for authentication. User metadata is synced from the directory. Groups can be used in access management.
Users defined in local user management can be migrated to users managed by Active Directory / LDAP.
Note
Once Active Directory / LDAP has been configured, it is not possible to switch back to local user management.
Important
Take a backup before changing the configuration to be able to revert.
Go to the 'Identity provider' section under the SECURITY menu.
Select the ‘Active Directory / LDAP’ option and click ‘Next step’.
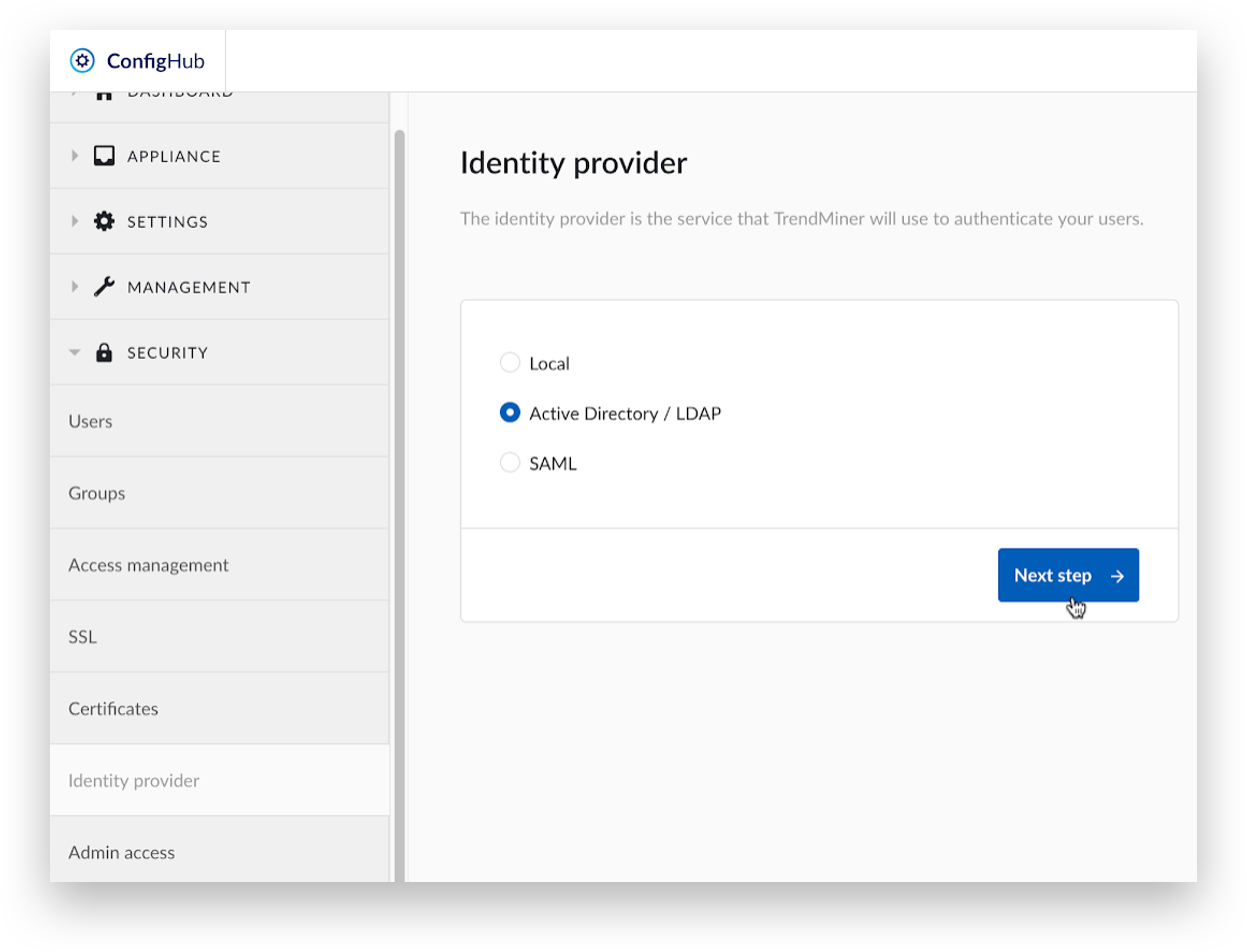
To allow rollback to the final non-AD/LDAP state, create a backup first, otherwise click ‘Next step’.
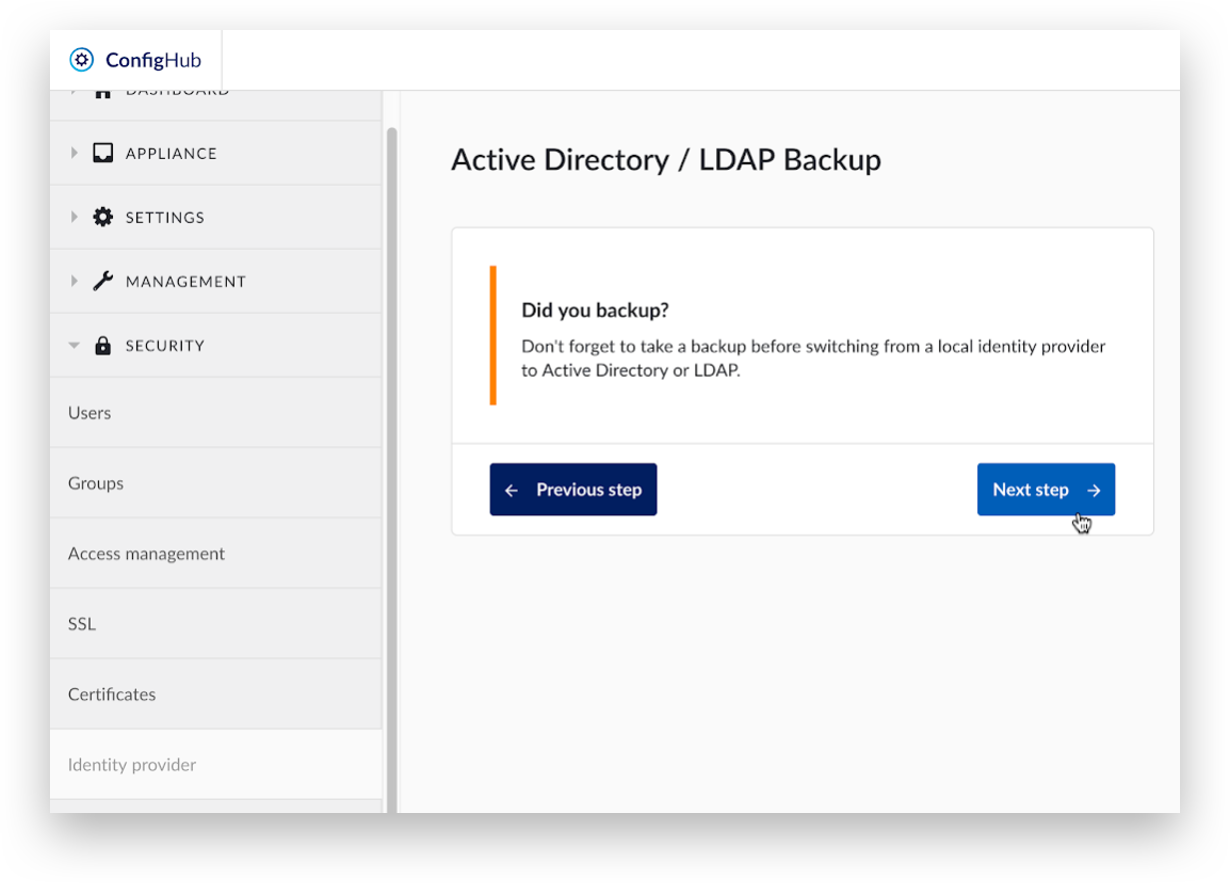
For LDAPS connections, one or more self-signed certificates could be required to connect to the LDAP server. Click 'here’ to go to the upload page for self-signed certificates or click ‘Next step’ to proceed.
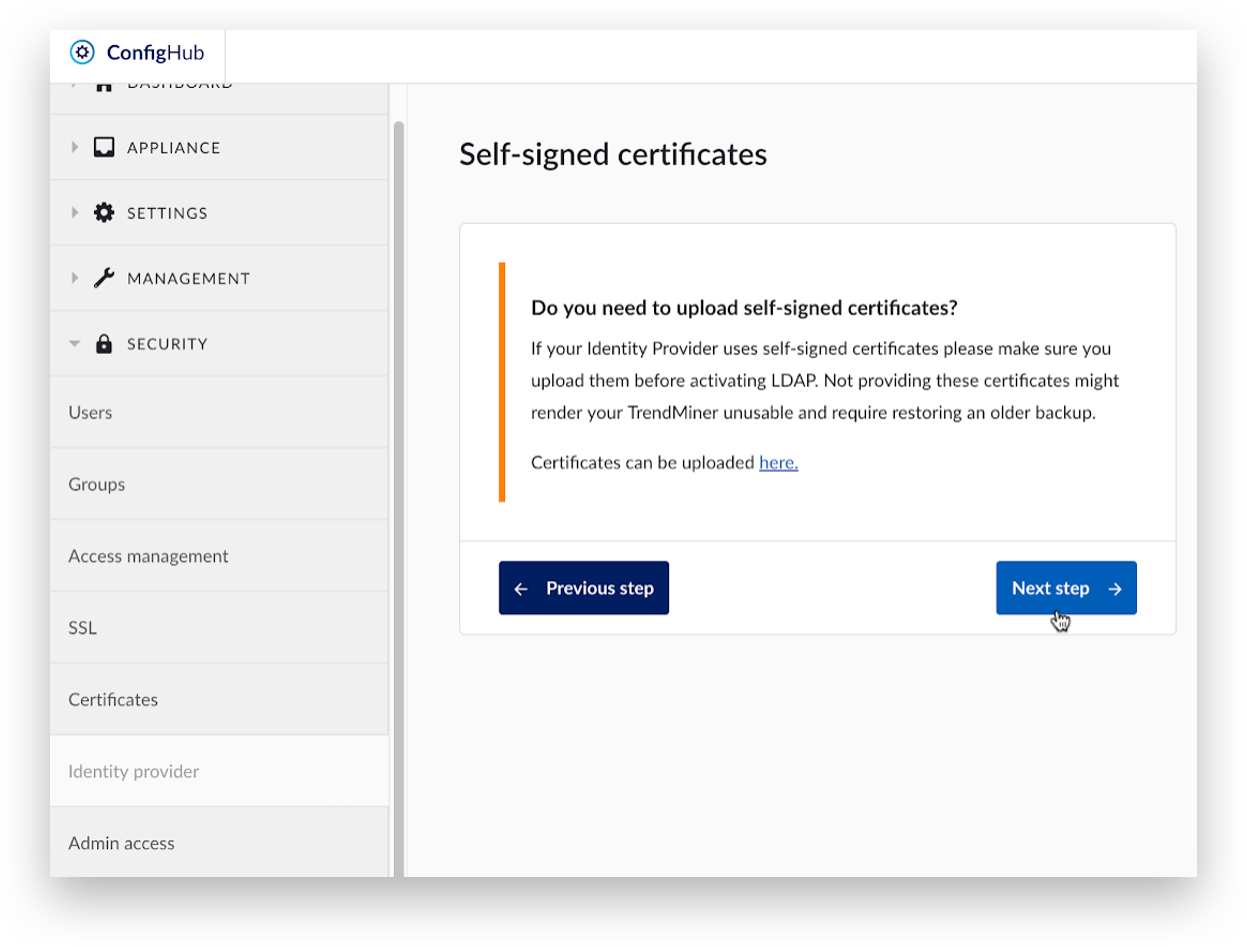
Fill Out the Active Directory / LDAP Configuration section.
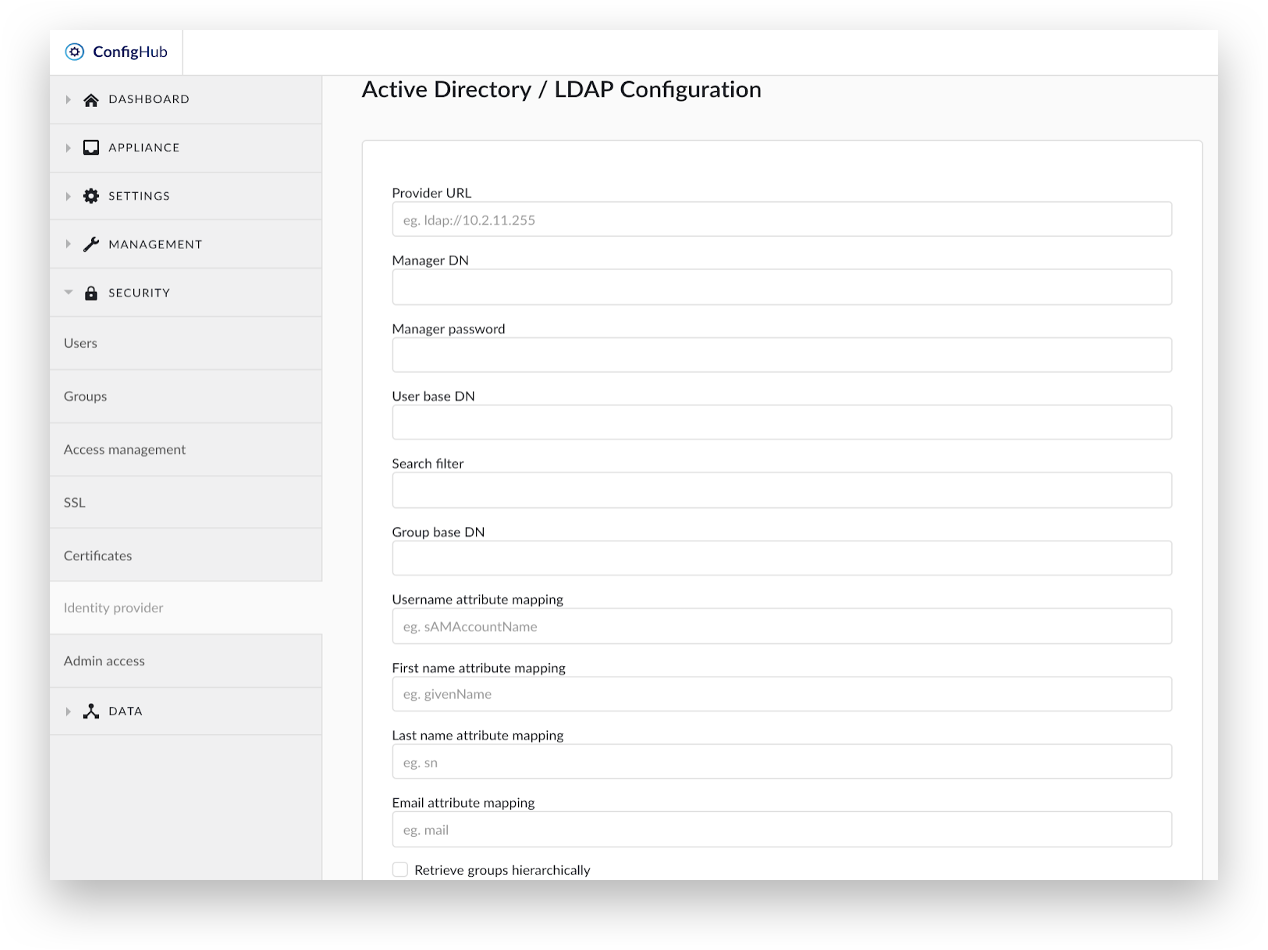
TrendMiner integrates with Active Directory / LDAP for user management and permissions management. Users are found by starting at a configurable point in the LDAP tree structure. TrendMiner will then recursively descend the tree and select users that match a given filter query.
Provider URL: The hostname of the LDAP server, including the protocol ldap://
Manager DN: The user that lists the users that will receive access to TrendMiner. This user must have query permissions on this server. It can be specified by full DN or by domain\user notation. Typically a ‘service’ account with a password that does not expire is used.
Manager password: The password of the user.
User base DN: The DN of the starting point of tree walking for users. All users must be descendants of this node.
Search filter: A filter to restrict the users that are permitted to access TrendMiner (eg. (objectCategory=Person) will select all users).
Group base DN: The DN of the starting point of tree walking for groups. Groups are used for permission management in TrendMiner. This does not influence which users are allowed access.
Username attribute mapping: The name of the attribute that represents the username of the user.
First name attribute mapping: This attribute points to the user's first name.
Last name attribute mapping: this attribute points to the user's surname or last name.
Email attribute mapping: mail address of the user.
Retrieve groups hierarchically: enable to descend the tree for groups starting at the Group base DN.
Testing and finishing
Click the 'Test connection' button to validate the configuration
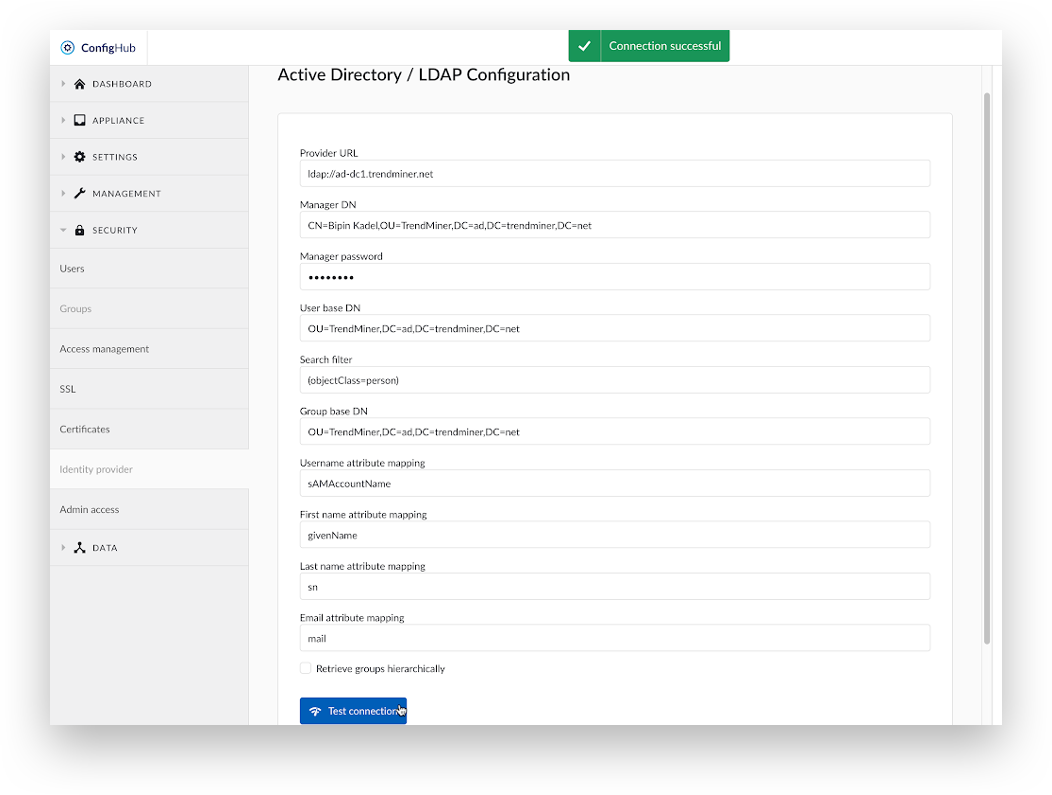
Click ‘Next Step’.
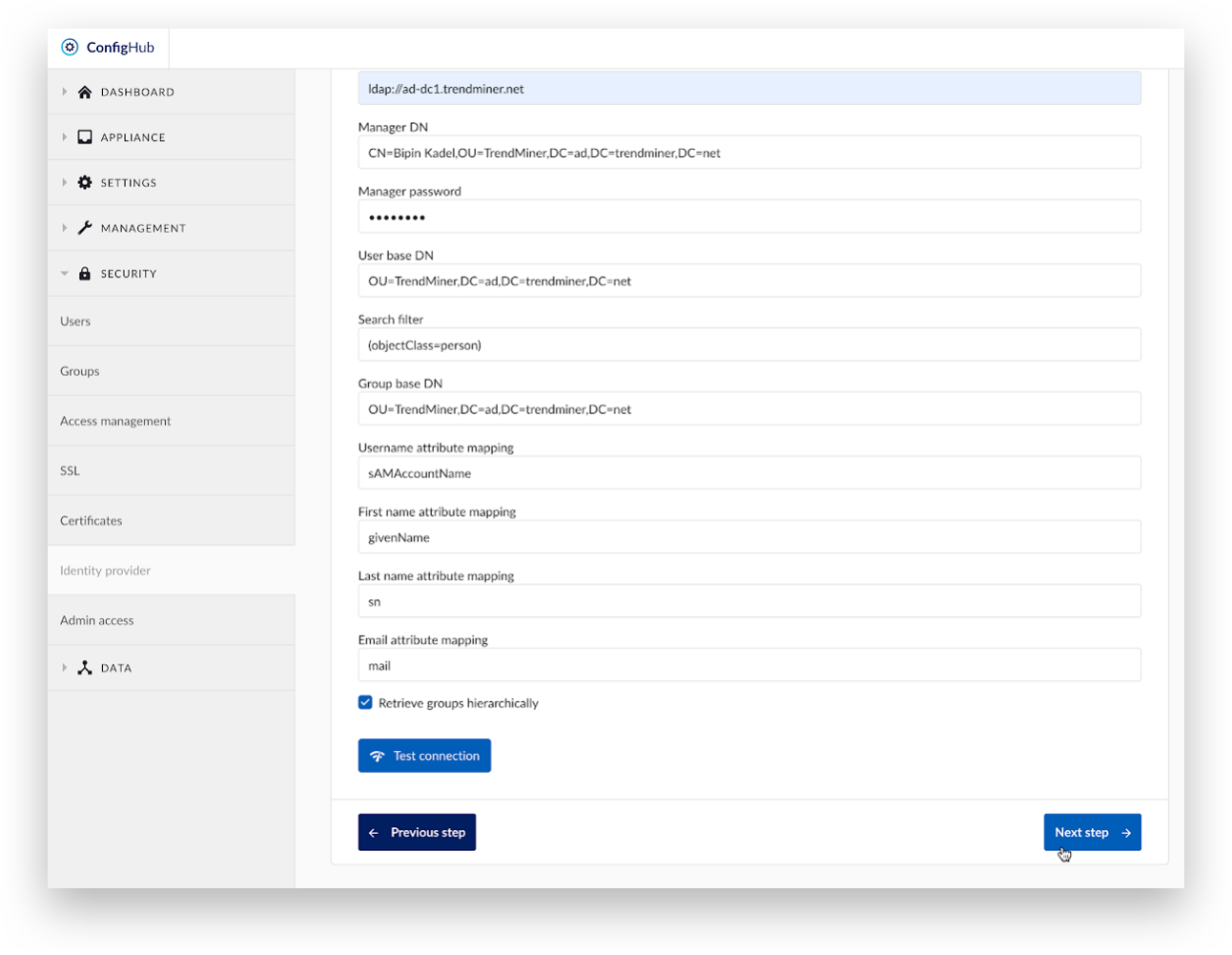
A 'Connection successful' message will display at the top of the screen.
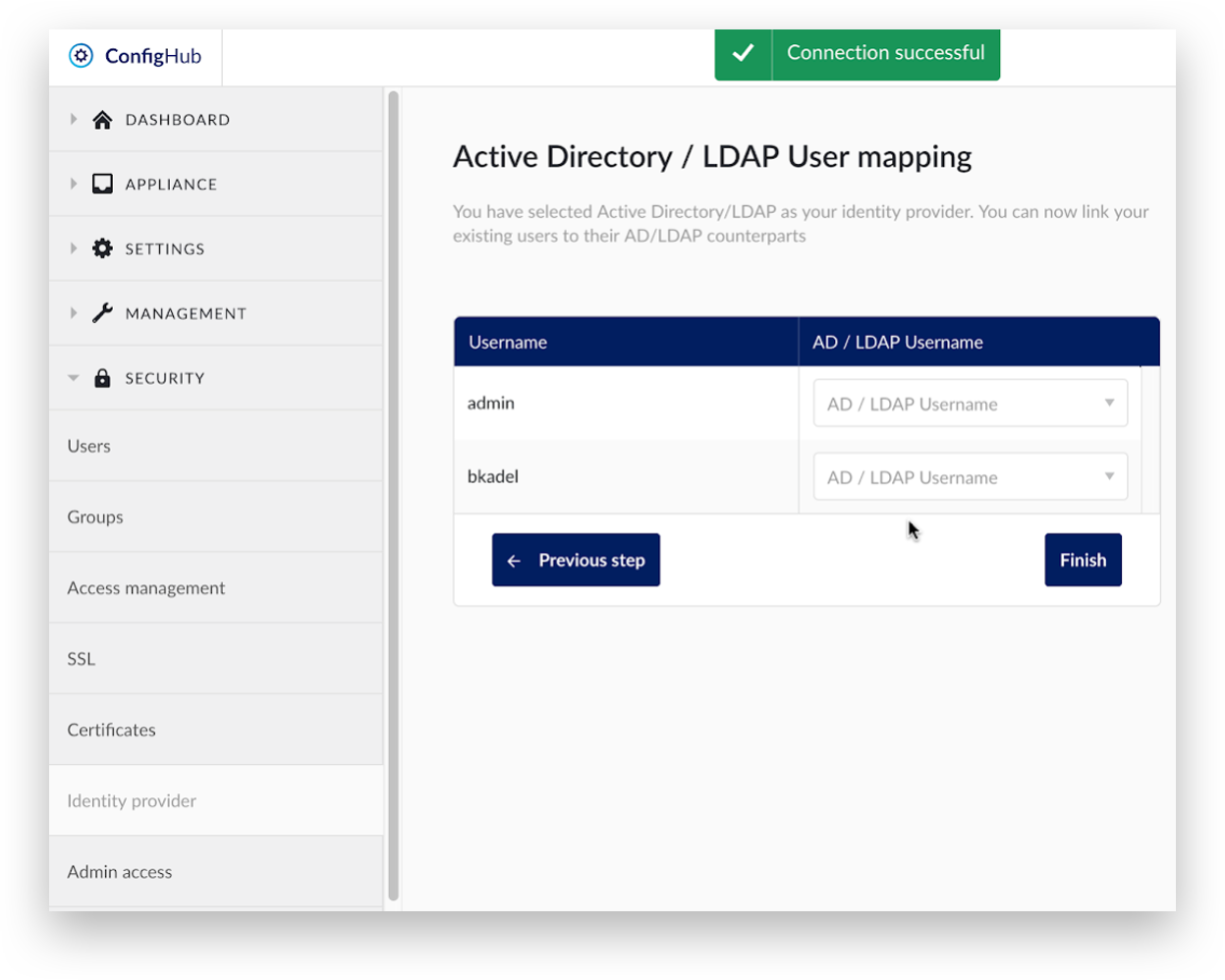
Select the corresponding Active Directory / LDAP user for each existing local user. Click ‘Finish’ to complete the user mapping.
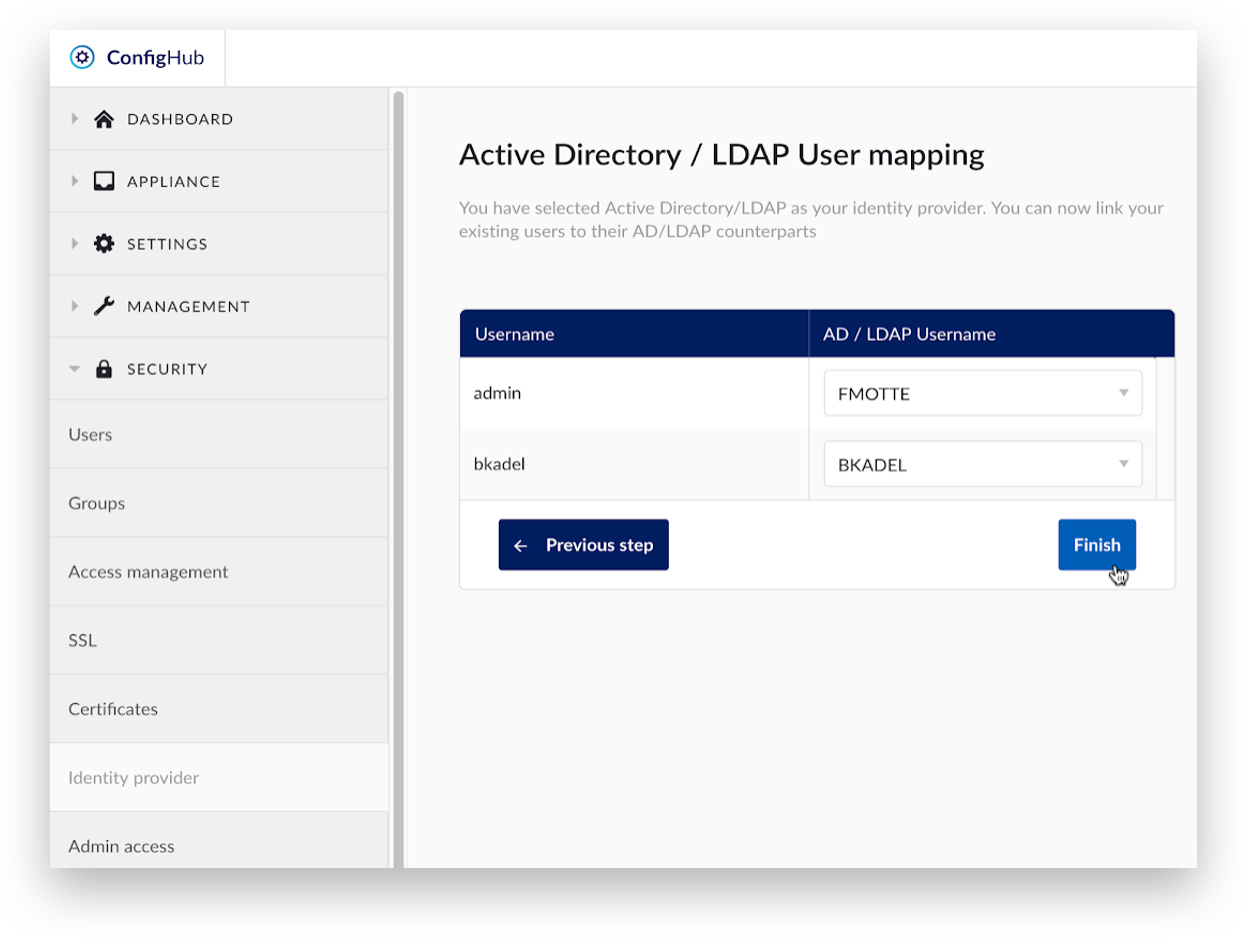
Click ‘Yes, map users’ to confirm the user mapping.
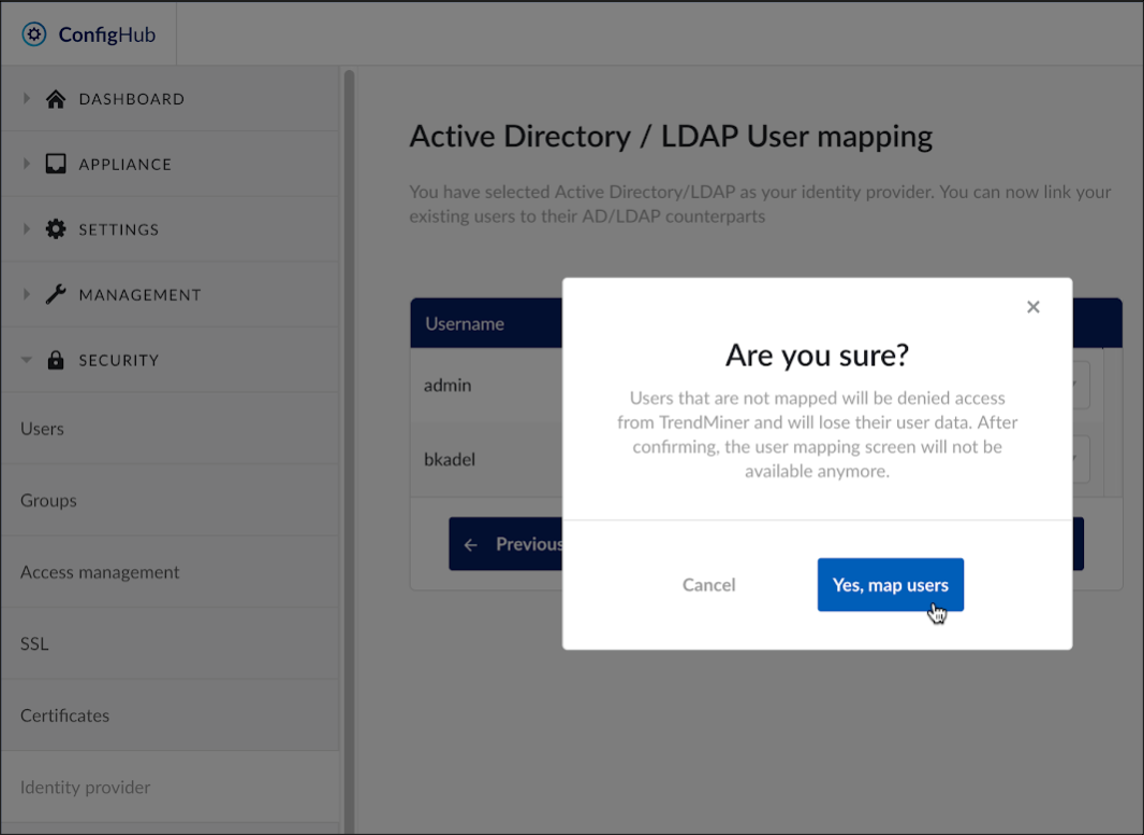
At the top of the screen, a message saying ‘Users have been mapped and will be available in a few minutes’ will display. Local users that are not mapped to an Active Directory / LDAP account will no longer be accessible.
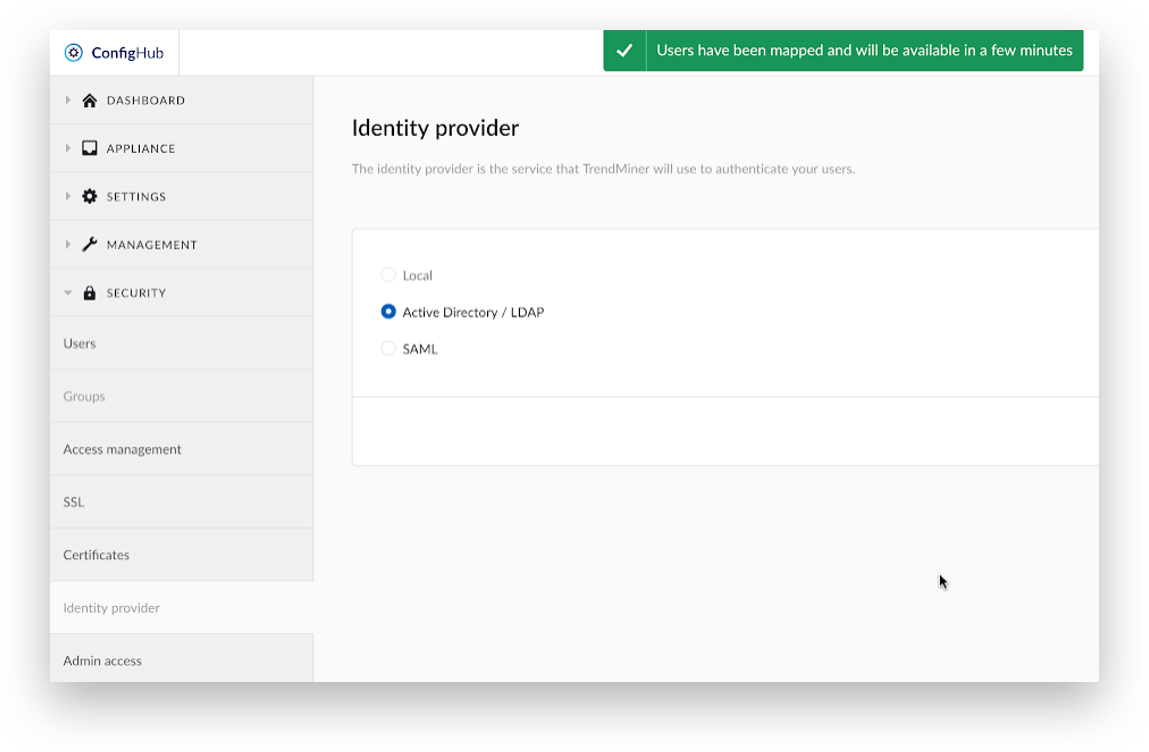
Please wait for 2-3 minutes and refresh the page. Click ‘Users’ under the ‘SECURITY’ menu to see the list of users. The ‘Groups’ option will be greyed out. TrendMiner synchronizes the list of users that will receive access rights every 5 minutes.
Log in to TrendMiner with Active Directory / LDAP credentials.

Active Directory Configuration Examples
Two example configurations are described here. A first case describes a simple configuration where users of one group receive access. A second case describes a more advanced configuration where users of multiple groups receive access.
Consider the following LDAP tree structure:
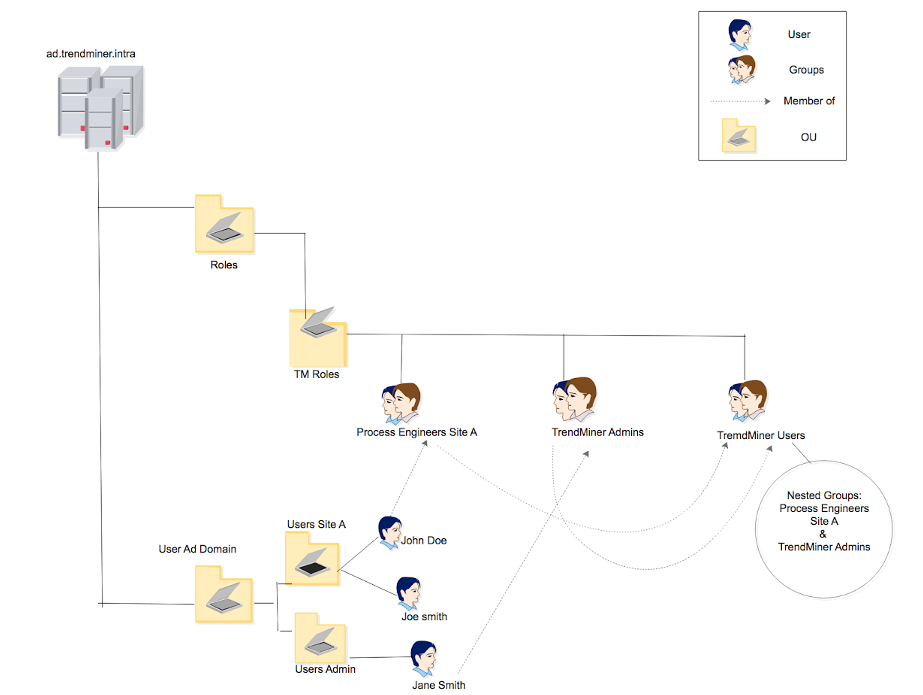
The Active Directory domain is ‘ad.trendminer.intra’.
All users are located under ‘Users AD Domain’. Users of production site A are defined in ‘Users Site A’. Global IT administrators are defined in ‘Users Admin’.
A separate hierarchy defines the roles of each user. All process engineers of Site A are added to a group ‘Process Engineers Site A’. All users that will receive administrative rights in TrendMiner are added in ‘TrendMiner Admins’.

Example 1: Users of one role are granted access.
Users in ‘TrendMiner Admins’ will be granted access to TrendMiner.
Since all users are located under ‘Users AD Domain’, this is a good DN to use as the User base DN in TrendMiner:
OU=Users AD Domain,DC=ad,DC=trendminer,DC=intra
The Search filter defines which users will be granted access. It is an LDAP filter. LDAP filters can include multiple criteria.
One criterion is that the object in the LDAP tree is a user. This is specified as: (objectClass=person)
Furthermore, the object should be a member of the TrendMiner Admins group:
(memberOf=CN=TrendMiner Admins,OU=TM Roles,OU=Roles,DC=ad,DC=trendminer,DC=intra)
Both criteria can be combined with a logical AND operator. This results with a full filter:
(&(objectClass=person)(memberOf=CN=TrendMiner Admins,OU=TM Roles,OU=Roles,DC=ad,DC=trendminer,DC=intra))
Since this is an Active Directory LDAP tree, the username is found in the sAMAccountName property of the user object.
This example can easily be extended to include users of multiple groups by adding a third criterion to the LDAP logical AND.
Example 2: Grant access to users in groups within groups (Active Directory only)
All users in the TrendMiner Users group will be granted access to TrendMiner. The TrendMiner Users group does not contain users directly, but includes users in TrendMiner Admins and in Process Engineers Site A.
Since all users are located under ‘Users AD Domain’, this is a good DN to use as the User base DN in TrendMiner:
OU=Users AD Domain,DC=ad,DC=trendminer,DC=intra
The Search filter defines which users will be granted access. It is an LDAP filter. LDAP filters can include multiple criteria.
One criterion is that the object in the LDAP tree is a user. This is specified as:
(objectClass=person)
The second criterion is that the user is a member of a group that is included in the TrendMiner Users role. The standard LDAP memberOf filter is not sufficient to handle this case. Active Directory provides an extension to the LDAP filter syntax to support this use case:
(memberOf:1.2.840.113556.1.4.1941:=CN=TrendMiner Users,OU=TM Roles,OU=Roles,DC=ad,DC=trendminer,DC=intra)
The full filter becomes:
(&(objectClass=person)(memberOf:1.2.840.113556.1.4.1941:=CN=TrendMiner Users,OU=TM Roles,OU=Roles,DC=ad,DC=trendminer,DC=intra))
Since this is an Active Directory LDAP tree, the username is found in the sAMAccountName property of the user object.