SAML
This section describes the required steps to enable SAML as Identity provider (IdP) for TrendMiner via ConfigHub. Examples for both OKTA and Azure are given.
Terminology
A Service Provider (SP) is the entity (TRENDMINER) providing the service, typically in the form of an application.
An Identity Provider (IdP) is the entity (OKTA/AZURE AD) providing the identities, including the ability to authenticate a user. The Identity Provider typically also contains the user profile: additional information about the user such as first name, last name, job code, phone number, address, and so on. Depending on the application, some service providers may require a very simple profile (username, email), while others may require a richer set of user data (job code, department, address, location, manager, and so on).
A SAML Request, also known as an authentication request, is generated by the Service Provider to "request" an authentication.
A SAML Response is generated by the Identity Provider. It contains the actual assertion of the authenticated user. In addition, a SAML Response may contain additional information, such as user profile information and group/role information, depending on what the Service Provider can support.
IdP settings Part 1
Azure AD
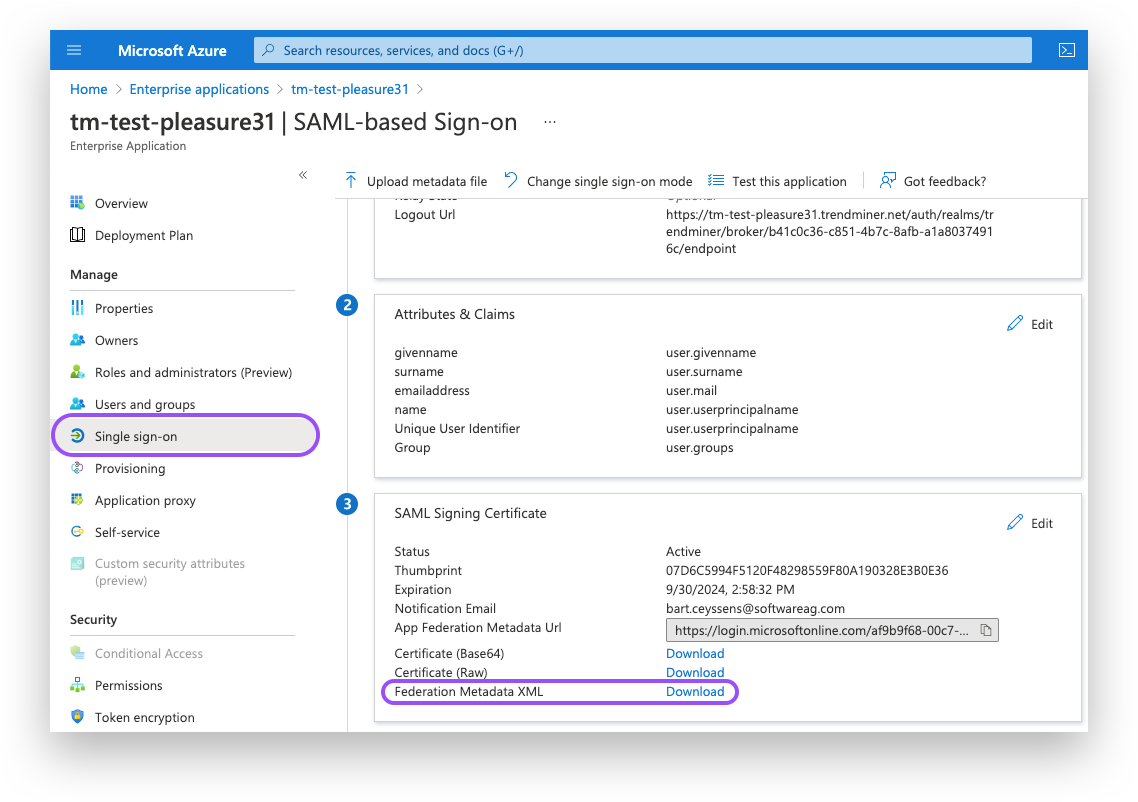
As a first step we'll need to download the Federation metadata XML from the IdP which will be uploaded later in TrendMiner's ConfigHub.
Aside from that, the user and security claims need to be setup correctly. With this configuration Azure AD will return the correct Subject in the response for use in TrendMiner.
Navigate in Azure AD to your SAML application and download the Federation Metadata XML. This file will be used to upload in TrendMiner ConfigHub in later steps.
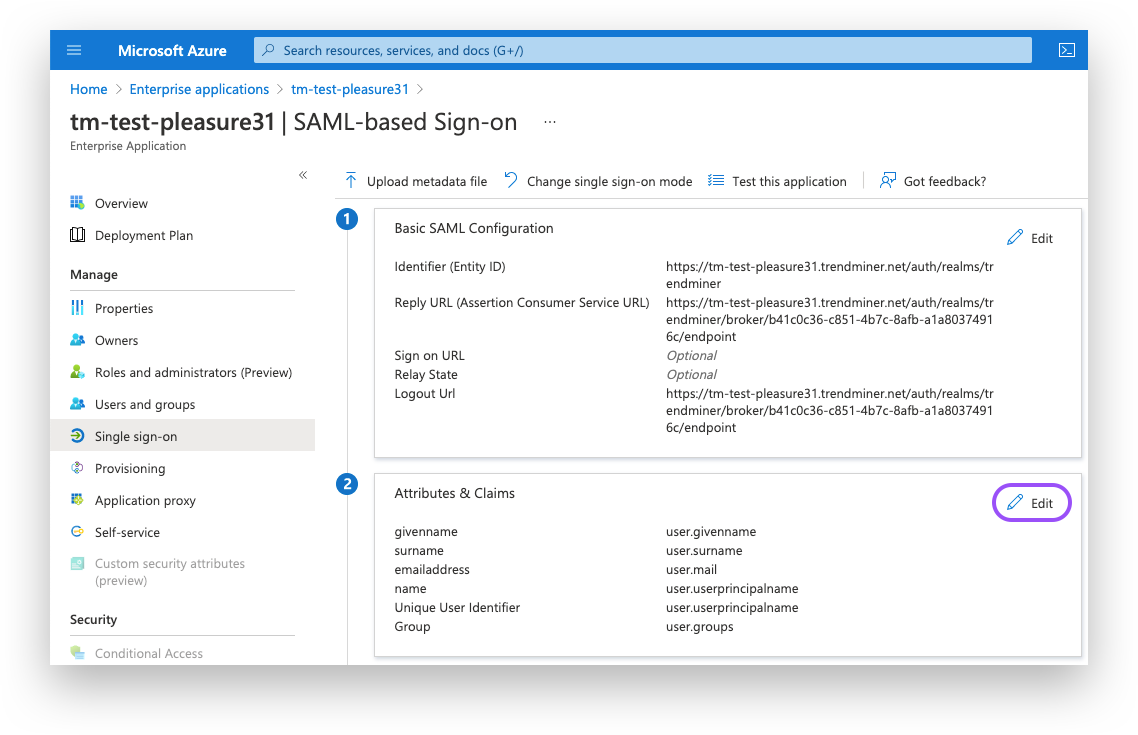
Configure user attributes & claims:
Click the "Edit"-button under "User Attributes & Claims"
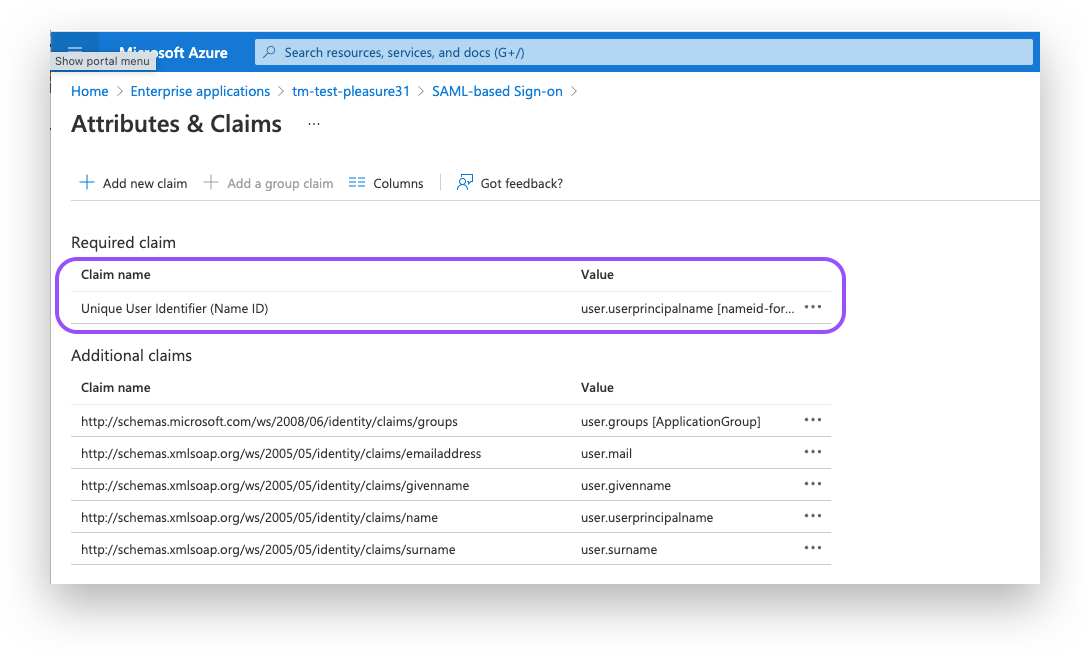
Click on the "Unique User Identifier (Name ID)" option.
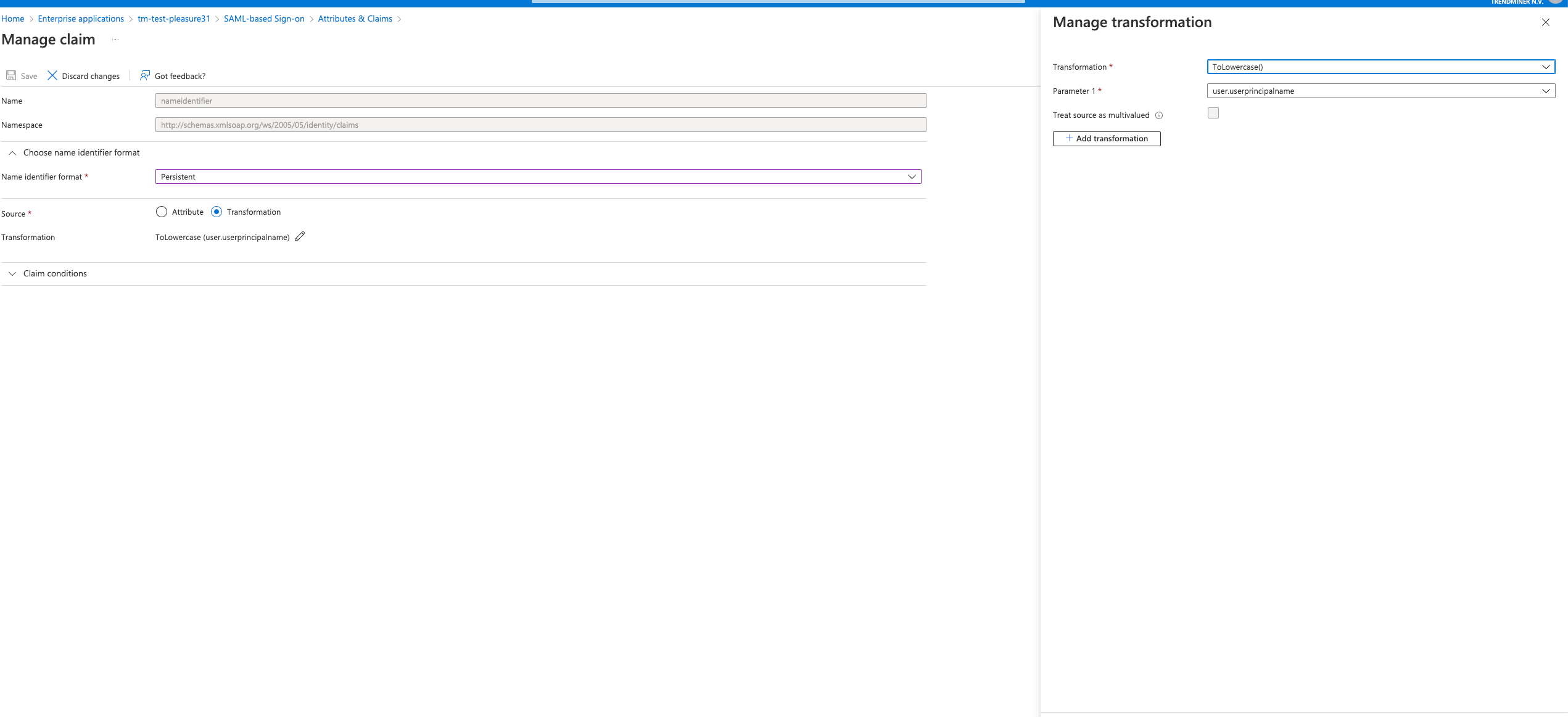
Make sure “Name identifier format” is set to a format of your choice. Note that the source attribute "user.userprincipalname" refers to the email in Azure. Under "Source" select ''Transformation" and add the "ToLowercase()" transformation for the "user.userprincipalname" as shown in the screenshot below.
Configure groups:
Click the "Edit"-button under "User Attributes & Claims"
Click the "Add a group claim"-option.
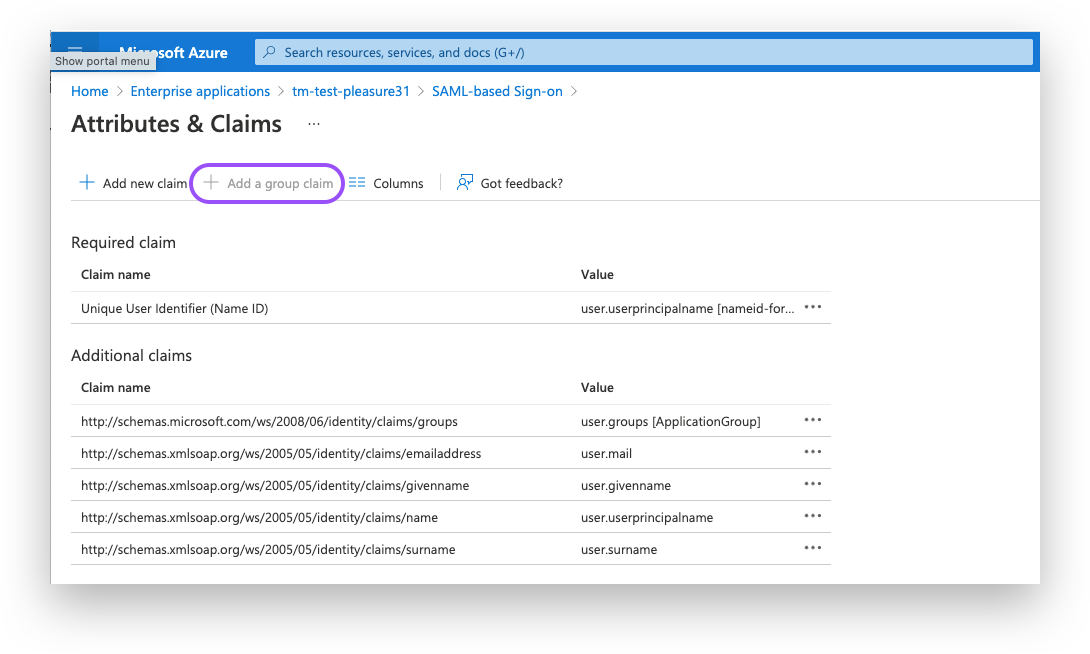
Set the Group Claims as shown on the screenshot below:
Associated: Groups assigned to the application.
Source attribute: Group ID
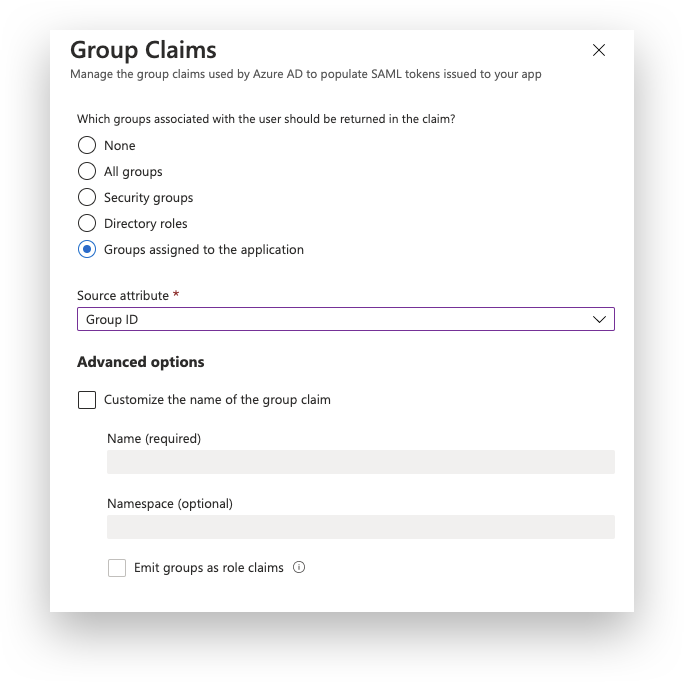
Add users/groups to the application.
Navigate to "the Users and Groups" tab.
Click the Add "user/group" button.
Continue with the steps for TrendMiners ConfigHub configuration as explained in the next section of this document.
OKTA
Create a new App Integration via the application menu.
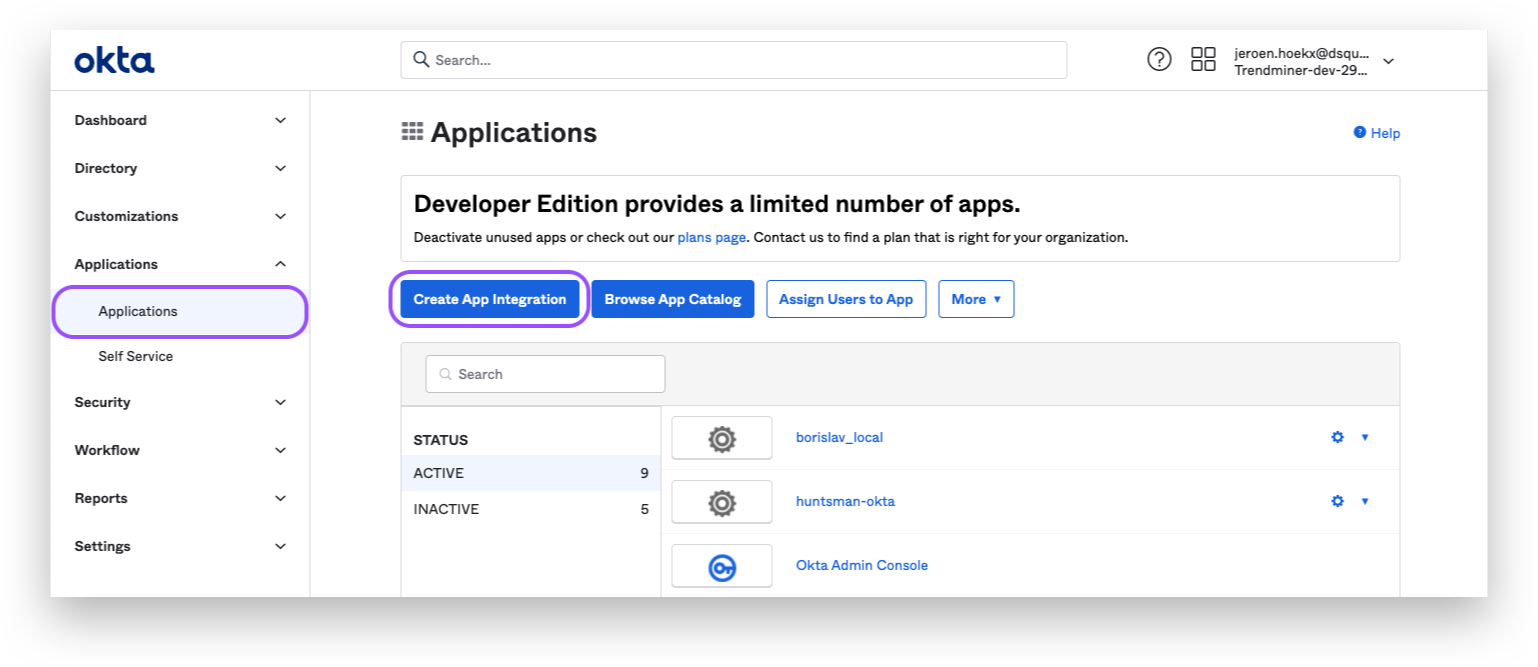
Choose the SAML2.0 option.
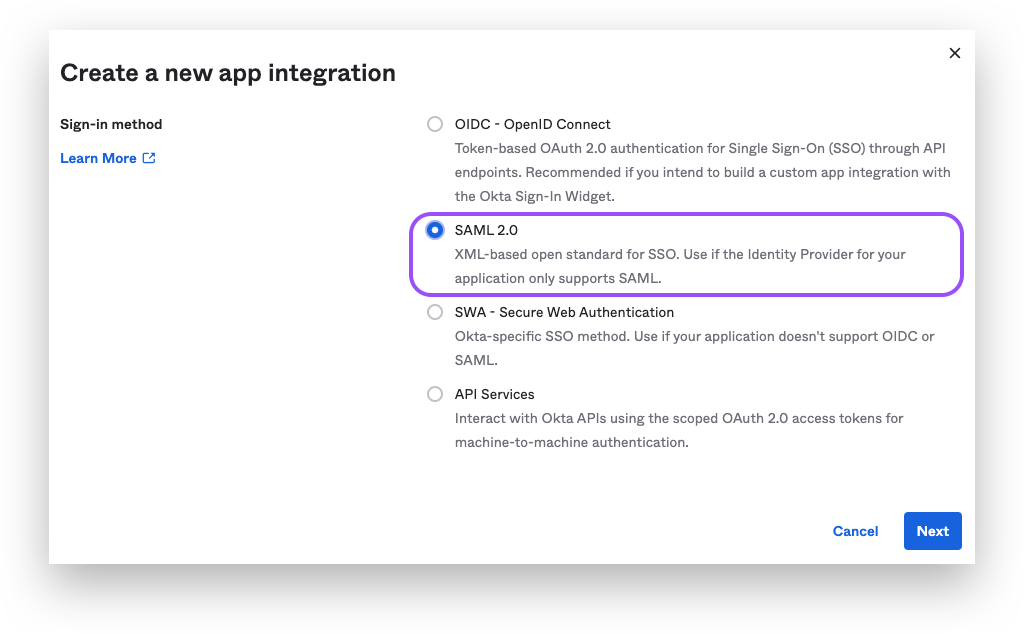
Fill in your "App Name" and click next.
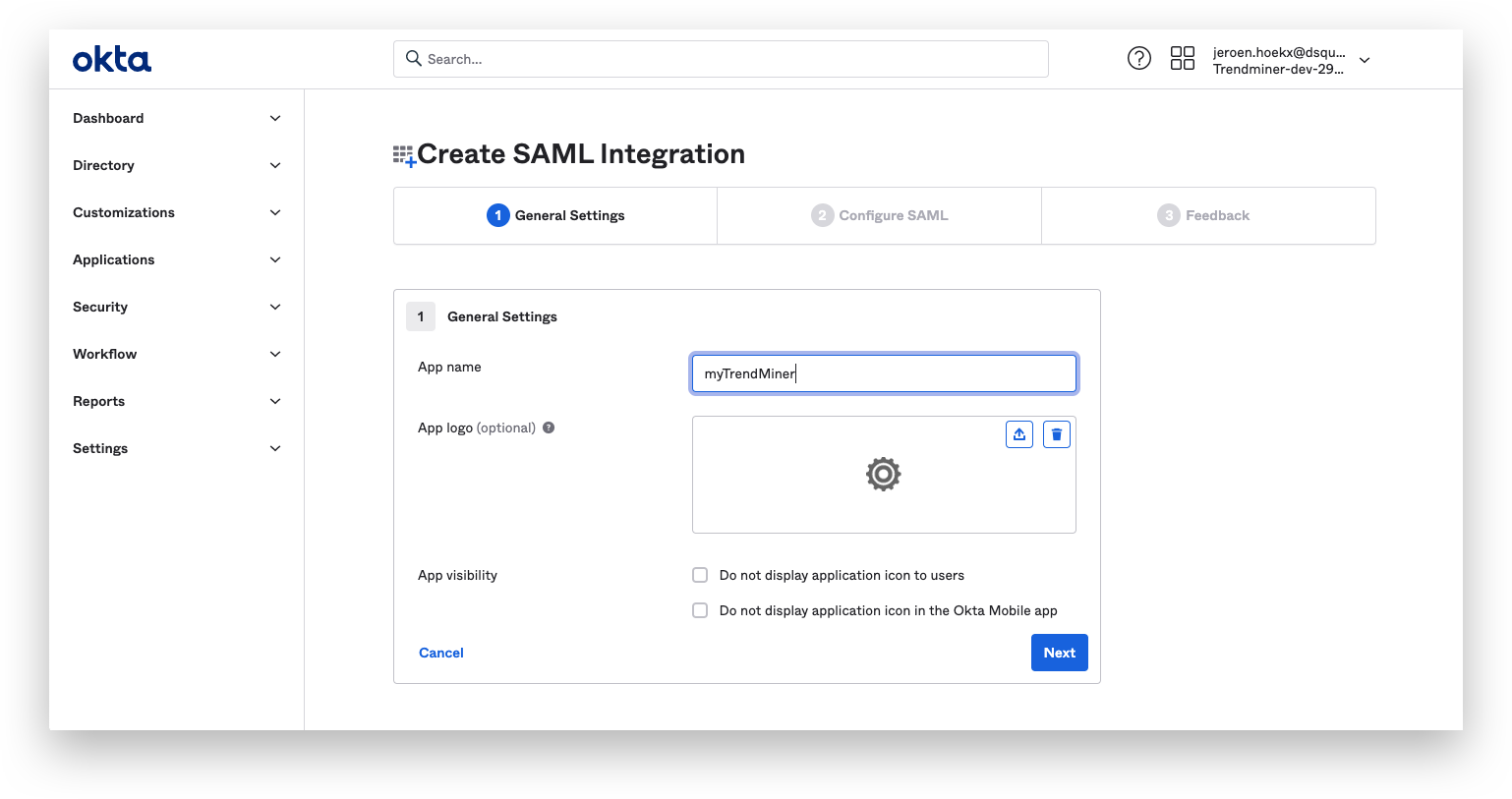
Fill out the details for the SAML settings and click on next when finished.
General settings:
Single sing on URL: This is just a temporary value which will be set at a later time.
Audience URI: This is just a temporary value which will be set at a later time.
Name ID format: Set to format of choice.
Application username: Okta username
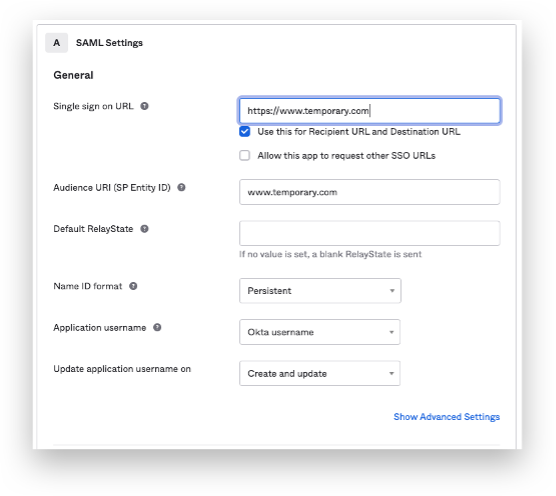
Add the following Attribute statements:
firstName / unspecified / user.firstName
lastName / unspecified / user.lastName
email / unspecified / user.email
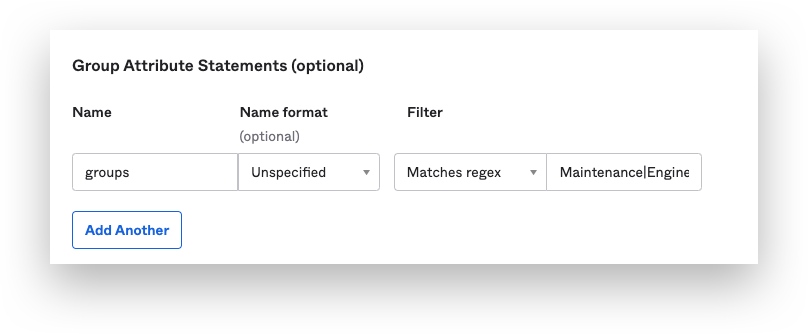
Add a Group statements:
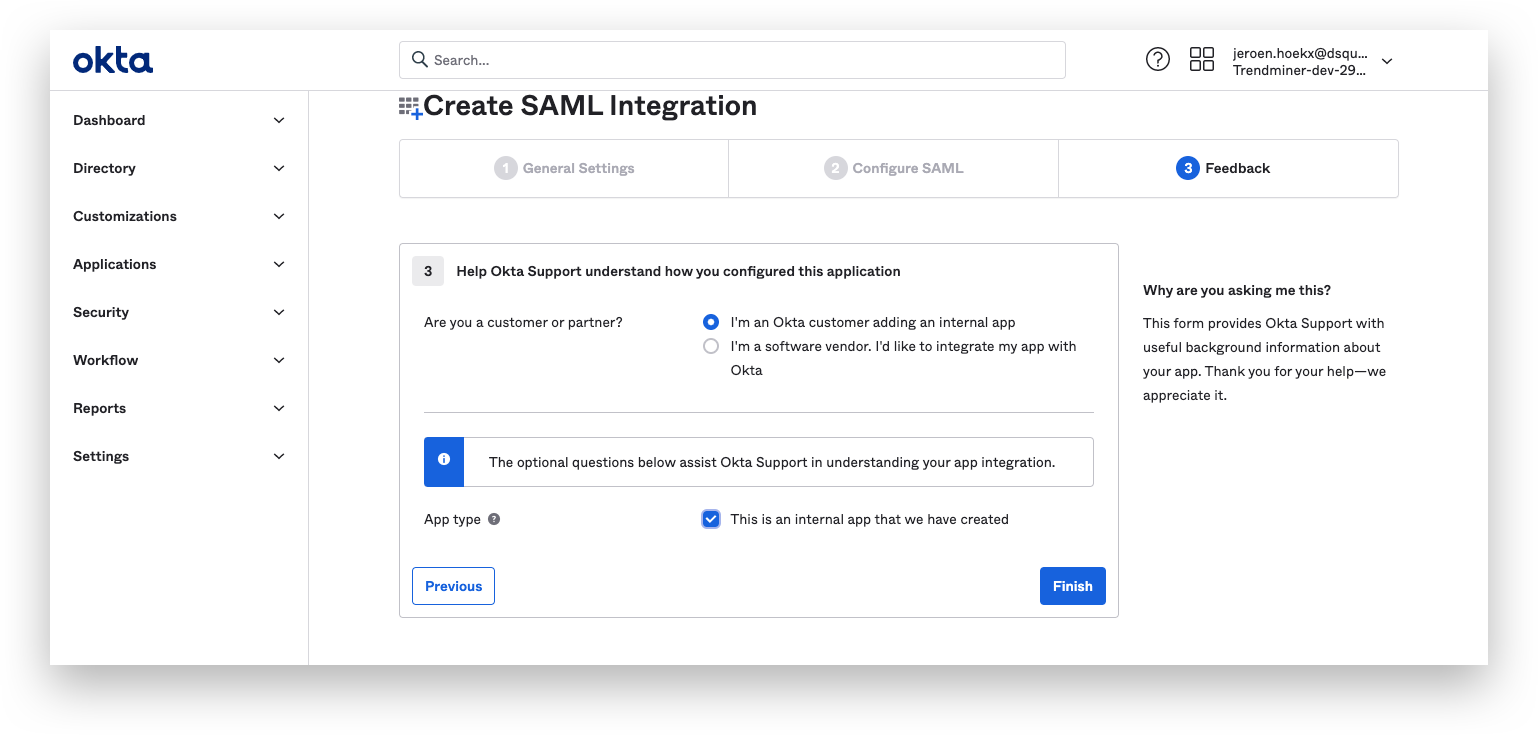
Select "I'm an Okta customer adding an internal app" + the "this is an internal app that we have created"-checkbox and click "Finish".
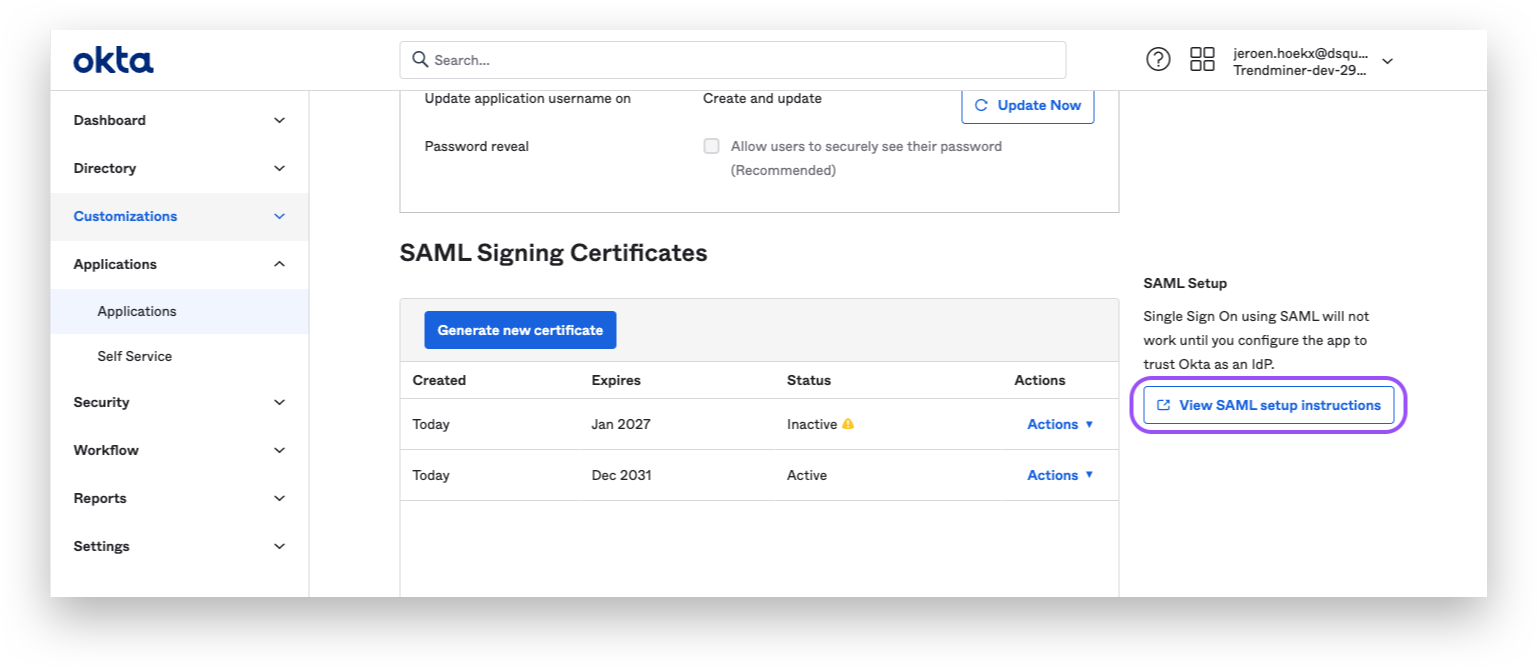
Fetch the Federation Metadata XML:
Click the "View SAML setup instruction"-button from the "sign on"-tab of your application.
Scroll down and copy the IDP metadata.
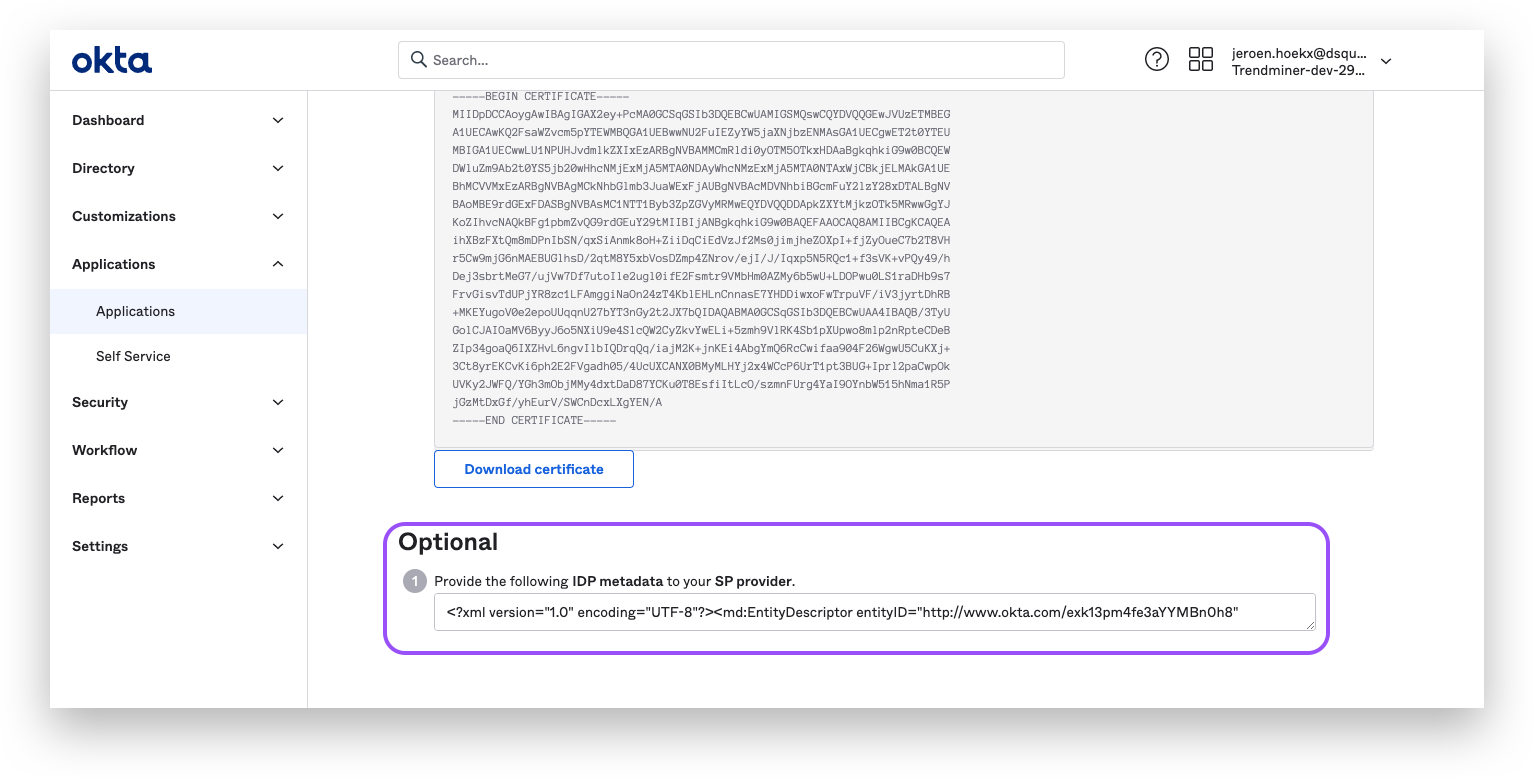
Paste the IDP metadata in a text-file and save with an ".xml"-extension.
Add users/groups to the application:
Open the "Assignments"-tab
Click on the "Assign"-button to add users/groups to the application
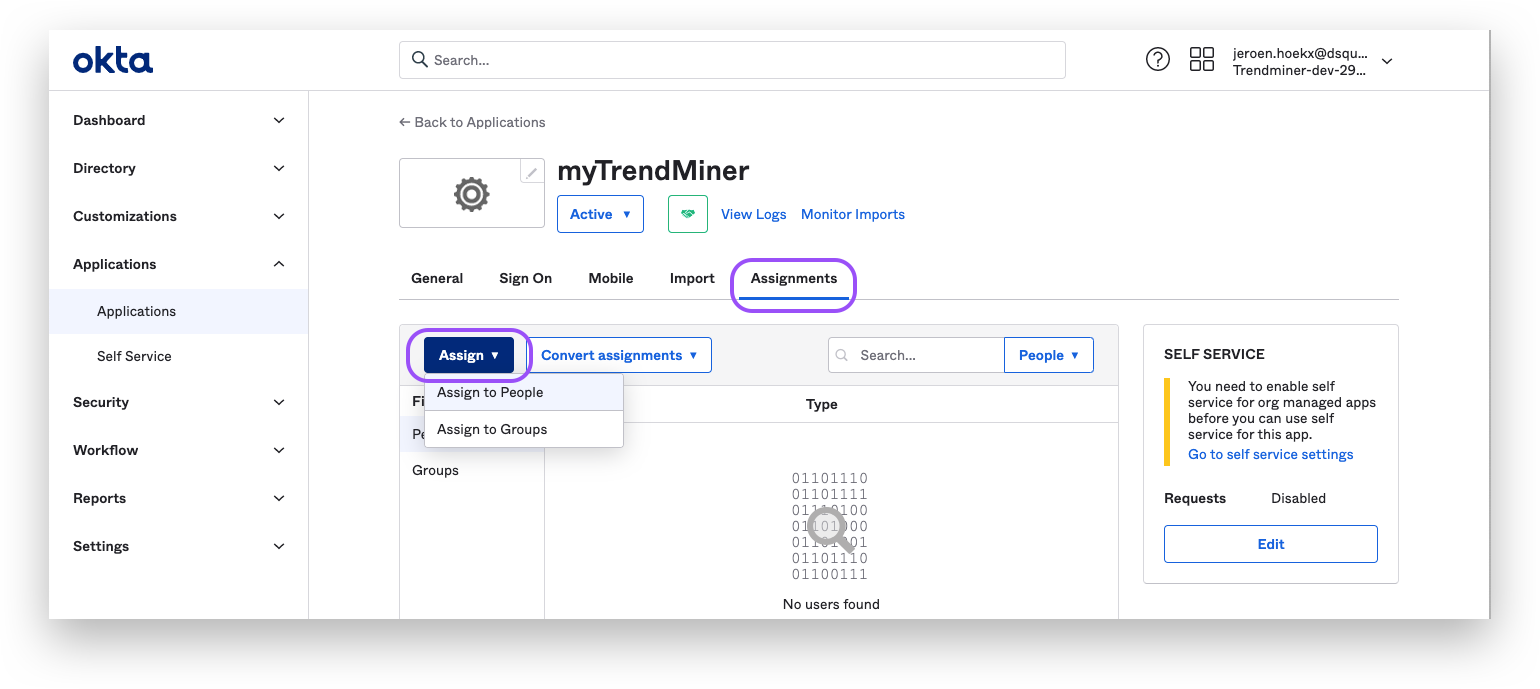
Continue with the steps for TrendMiners ConfigHub configuration as explained in the next section of this document.
TrendMiner ConfigHub configuration
After setting up the initial application in AZURE/OKTA we can continue in TrendMiner's ConfigHub. Via ConfigHub we can see an overview of the existing Identity Providers and have the ability to configure a new one.
Navigate to ConfigHub and open the "Identity Providers" tab in the "Security" section.
Click the "Add provider"-button.
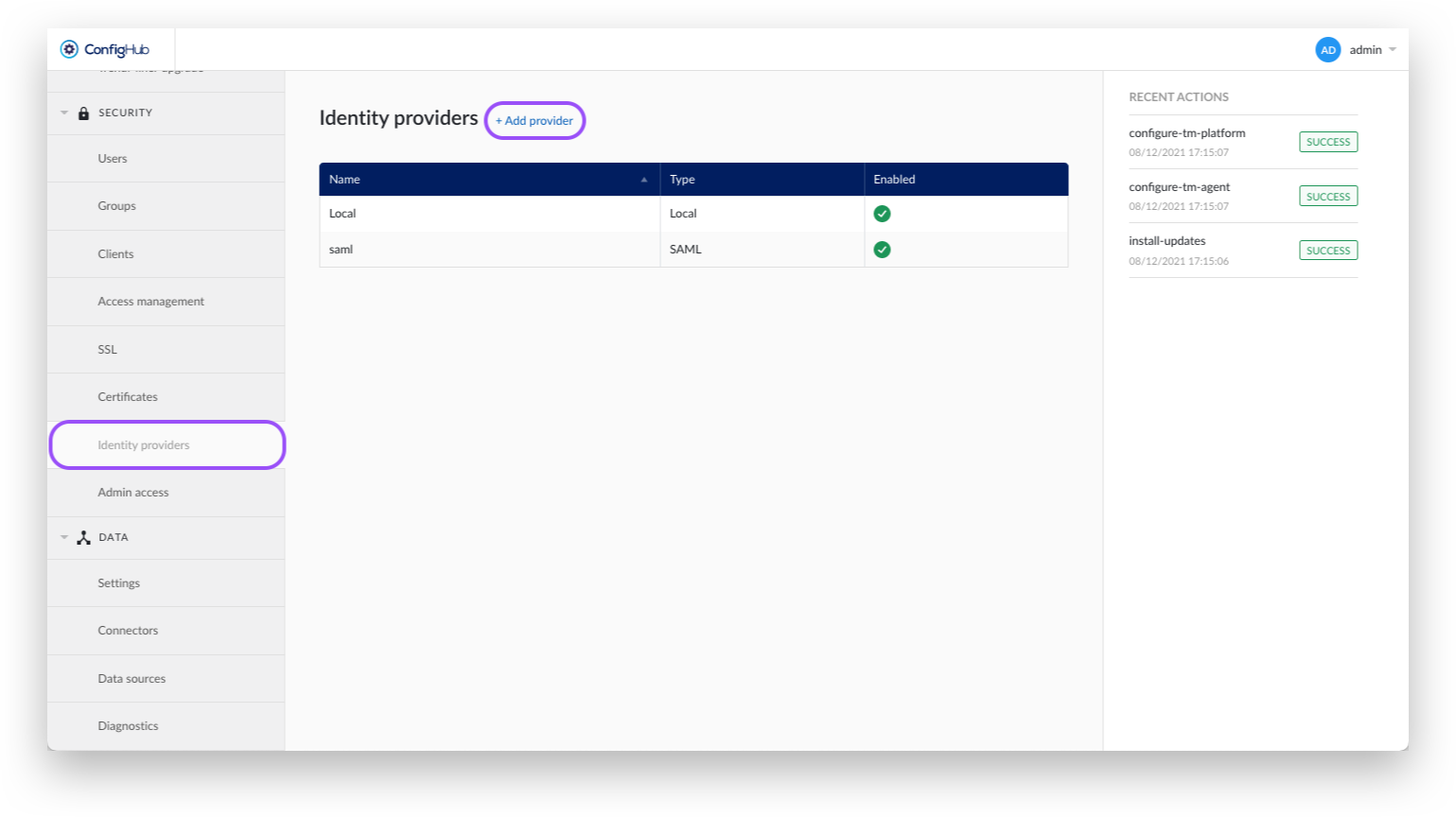
Select the SAML option.
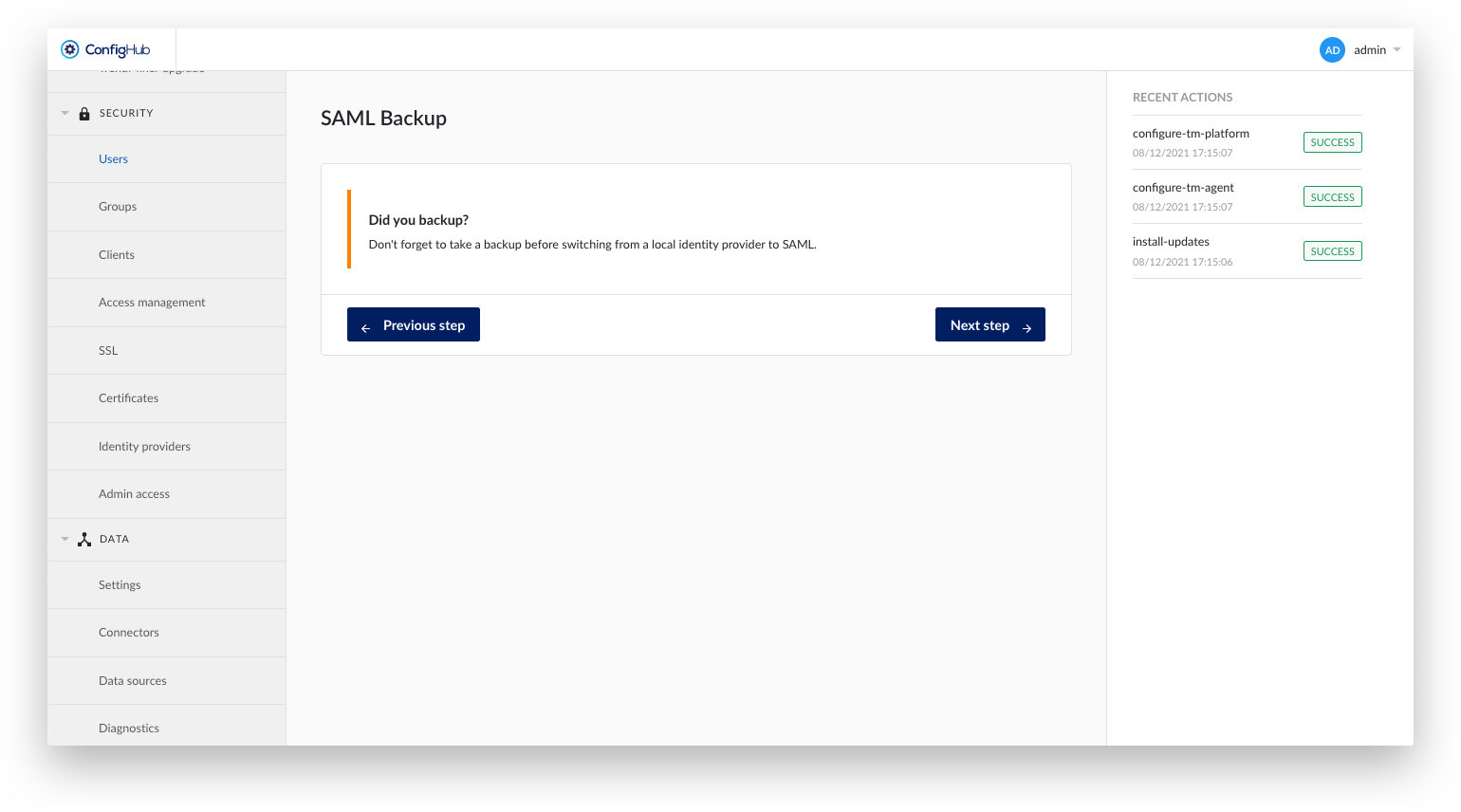
Create a TrendMiner backup.
Upload a Self-signed certificate if necessary. Self-signed certificates might be necessary if the IDP uses a custom CA certificate over HTTPS.
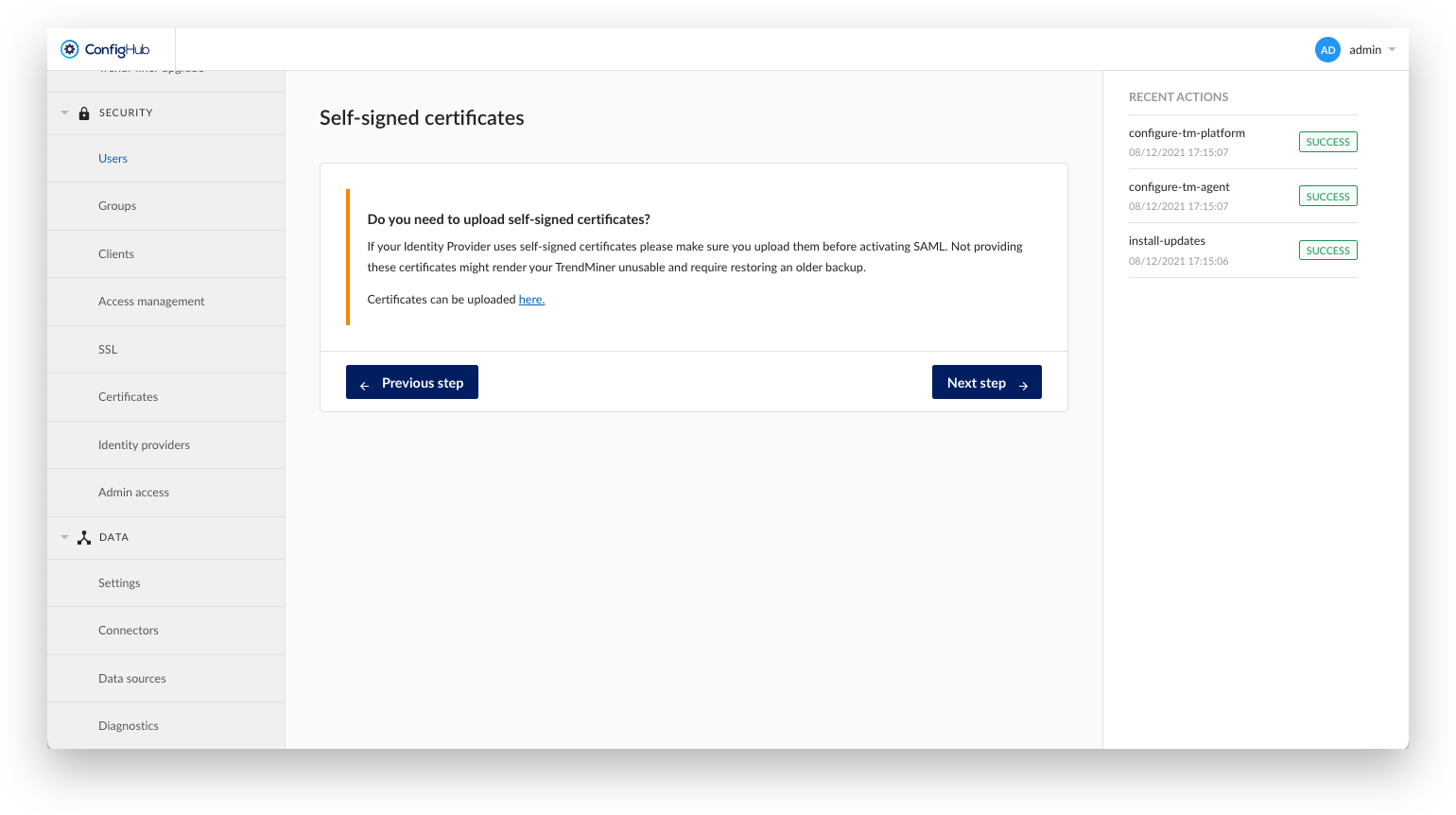
Indicate whether this service provider expects a signed Assertion.
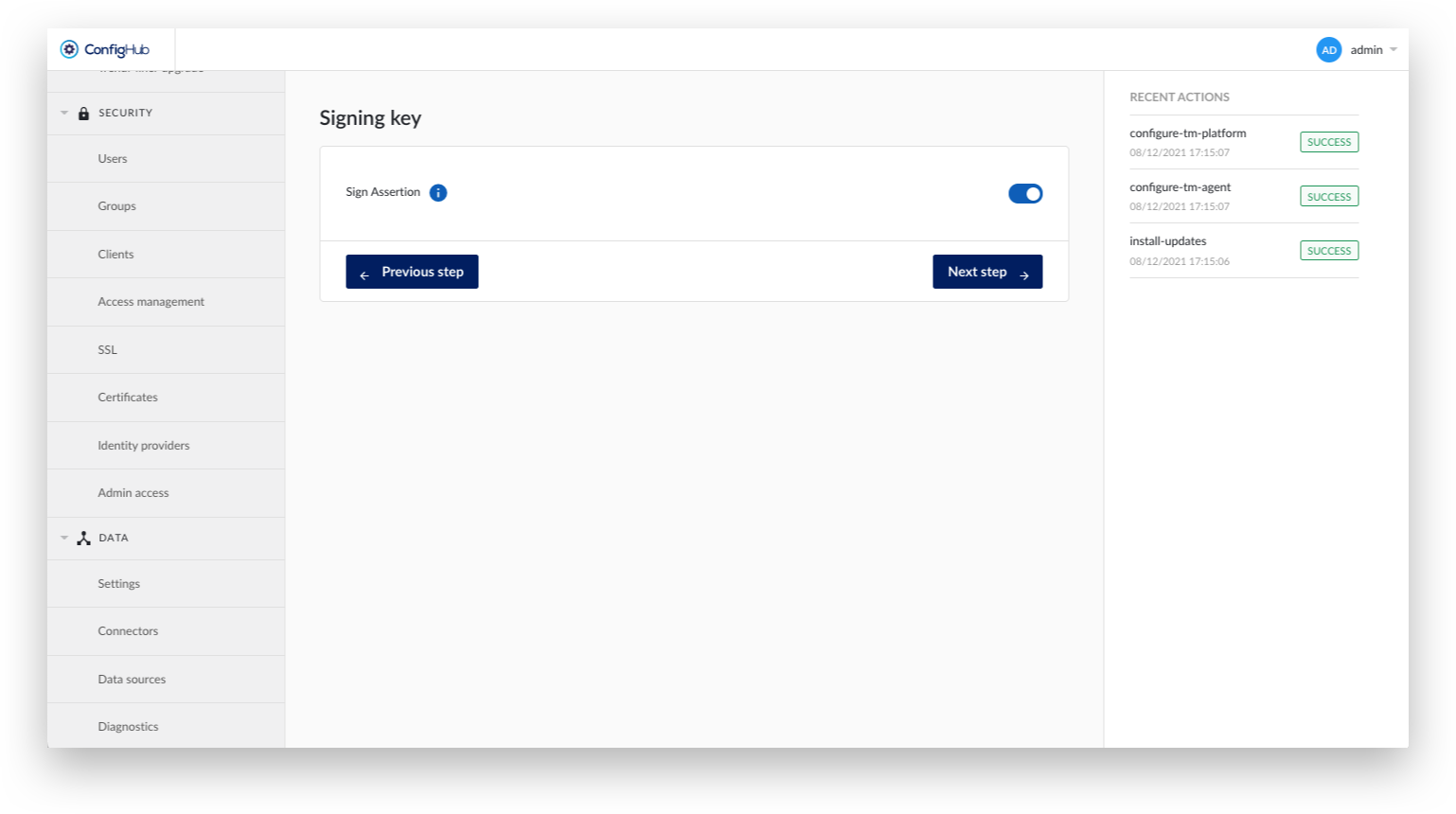
Fill out the details for the SAML configuration:
Name: Display name in ConfigHub and used as root group. Does not relate to any technical SAML details.
Base domain: Used in URLs of the SP metadata file. Eg: where the IDP has to redirect after identification.
NameID Policy Format: A dropdown to select the policy format as being used by the customer SAML provider (f.ex. Azure, Okta). Possible values are: Persistent, Transient, Email, Kerberos, X.509 Subject Name, Windows Domain Qualified Name, Unspecified
Principal Type: A dropdown to select the principal type as being used by the customer SAML provider (f.ex. Azure, Okta). Possible values are: Subject name ID, Attribute name, Attribute friendly name
Principal Attribute: In case attribute name or attribute friendly name was selected as an option from the Principal Type dropdown a extra input field will become visible to allow to enter the name of the specific attribute to be used
Identity provider metadata file: Upload the Federation Metadata XML file you have downloaded from the IdP in the previous section.
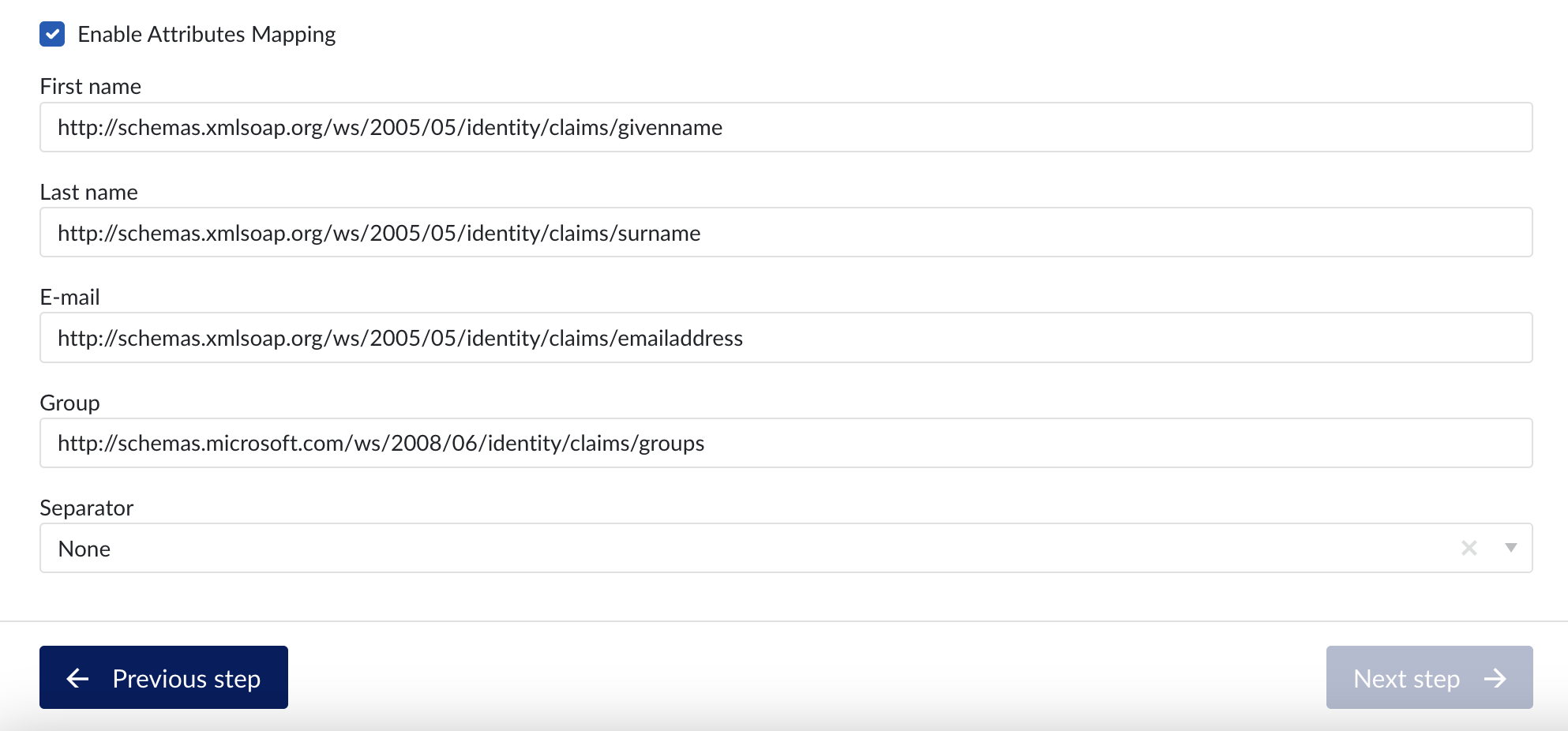
Enable Attributes Mapping: Optional setting to map SAML assertions into ConfigHub. Note that the mappings needs to correspond with the attribute names used from the IdP (see previous section). For Azure this corresponds to the the claim name (e.g. http://schemas.microsoft.com/ws/2008/06/identity/claims/groups) while for Okta this corresponds to the given names in the previous steps (e.g. firstName, groups,…).
The next screens allows to map existing (local) TrendMiner users to the SAML provider. The SAML username should correspond to the value returned by the IdP in the Subject-NameID tags. TrendMiner requests the NameId in format:
"urn:oasis:names:tc:SAML:2.0:nameid-format:persistent".
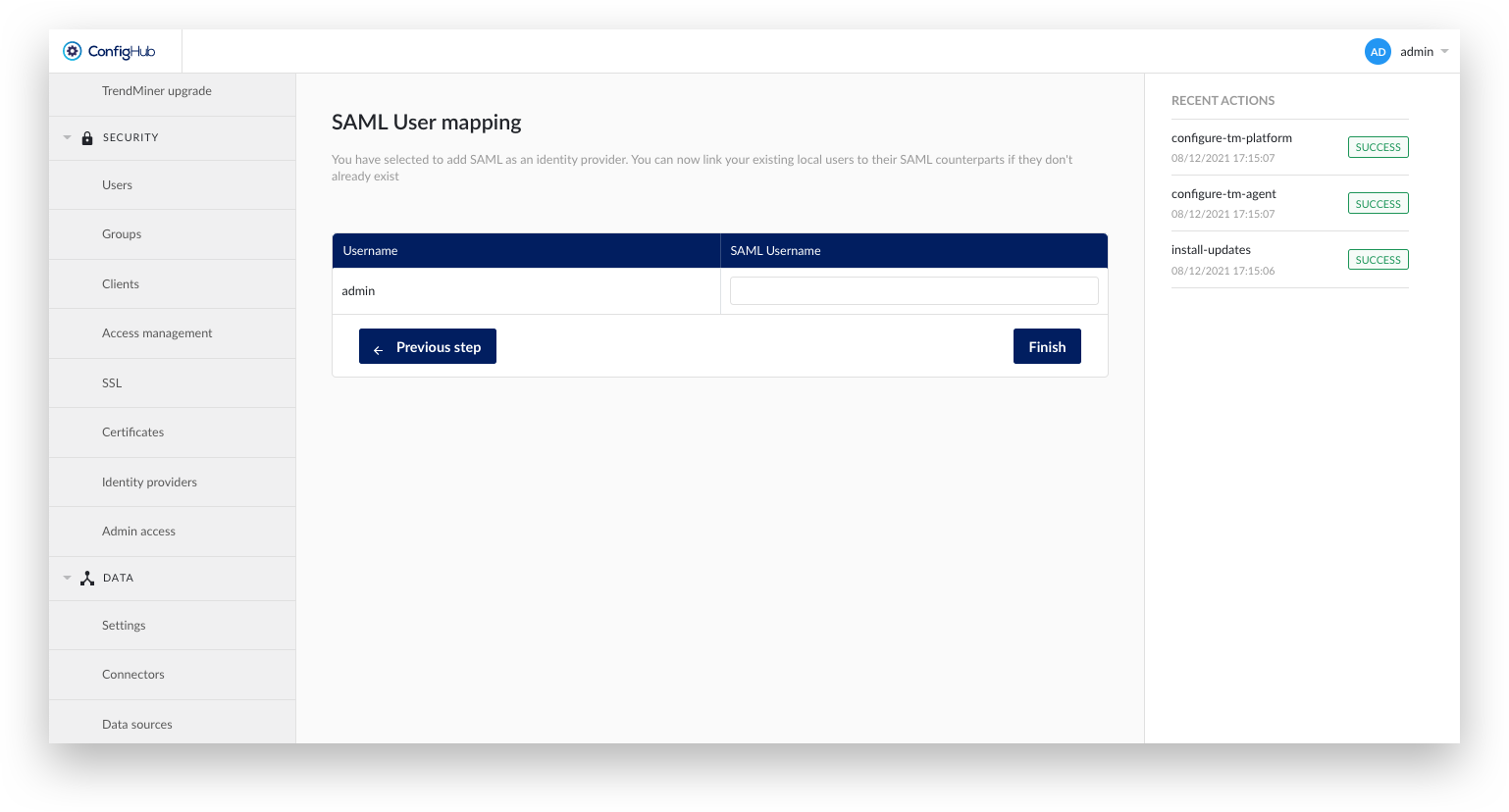
After creating the identity provider in ConfigHub it is time to download the metadata file and go back to Azure AD or Okta..
Go back to the "Identity Providers" tab in the "Security" section in ConfigHub. You should be able to see your created provider listed.
Click on your newly created provider. A side-panel should pop-up.
Click the options-button
Click the download Metadata button. This metadata file contains the remaining configuration on the IdP side.
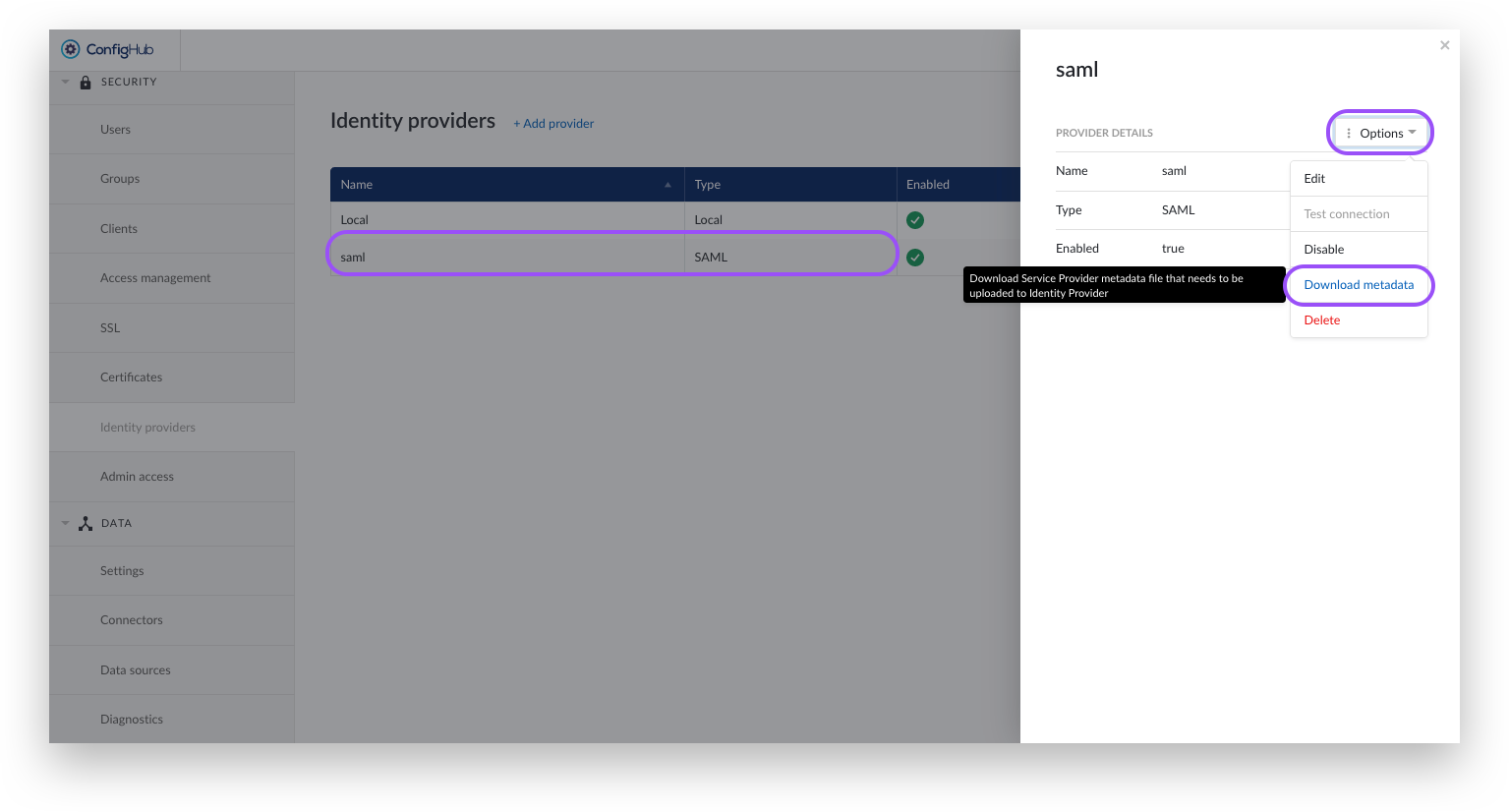
Continue with the configuration in Azure AD or Okta as explained in the next section.
IdP settings Part 2
Now that we have the metadata file from TrendMiner we can proceed with the finalizing the configuration on the IdP side.
Azure AD
Navigate in Azure AD to your SAML application and open the "Single sign-on"-tab.
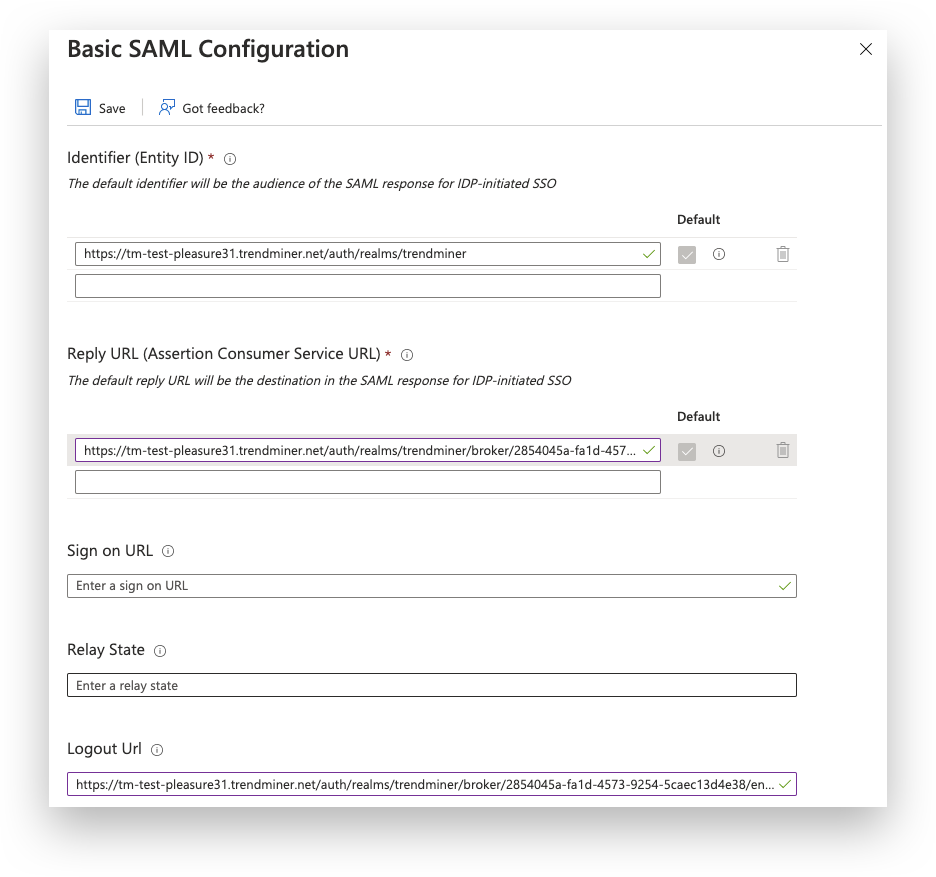
Click the "Upload metadata file" and upload the TrendMiner metadata file.
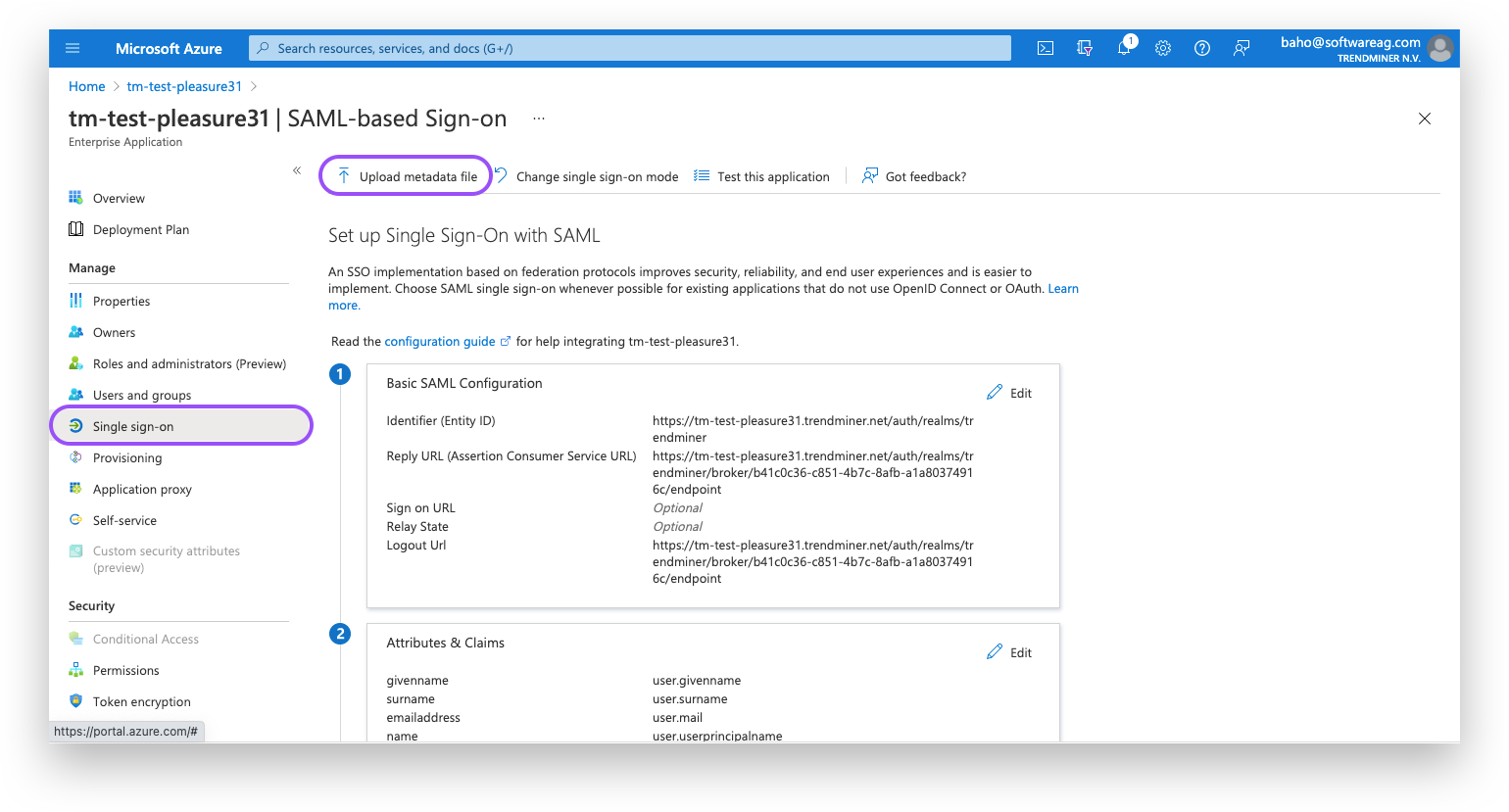
It might be necessary to fill in the Reply URL yourself. This is the same value as Logout URL.

The SAML setup is complete and you should be able to login in TrendMiner. After logging in with a SAML user in TrendMiner the assigned groups should be synced and ACLs can be configured.
OKTA
OKTA does not support uploading SP metadata files so some manual extraction is necessary.
Open the metadata file from TrendMiner in a text-editor. The metadata should like this:
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" xmlns="urn:oasis:names:tc:SAML:2.0:metadata" xmlns:ds="http://www.w3.org/2000/09/xmldsig#" xmlns:saml="urn:oasis:names:tc:SAML:2.0:assertion" ID="ID_3f7843b9-664f-40e7-a536-2fa8893e87b6" entityID="https://trendminer.example.com/auth/realms/trendminer"> <md:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol"> <md:SingleLogoutService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://trendminer.example.com/auth/realms/trendminer/broker/7fc6524e-3d55-4ae2-9edf-3d678e376063/endpoint"/> <md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat> <md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-POST" Location="https://trendminer.example.com/auth/realms/trendminer/broker/7fc6524e-3d55-4ae2-9edf-3d678e376063/endpoint" index="1" isDefault="true"/> <md:AttributeConsumingService index="1" isDefault="true"> <md:RequestedAttribute FriendlyName="lastName" Name="lastName" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/> <md:RequestedAttribute FriendlyName="email" Name="email" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/> <md:RequestedAttribute FriendlyName="firstName" Name="firstName" NameFormat="urn:oasis:names:tc:SAML:2.0:attrname-format:basic"/> </md:AttributeConsumingService> </md:SPSSODescriptor> </md:EntityDescriptor>
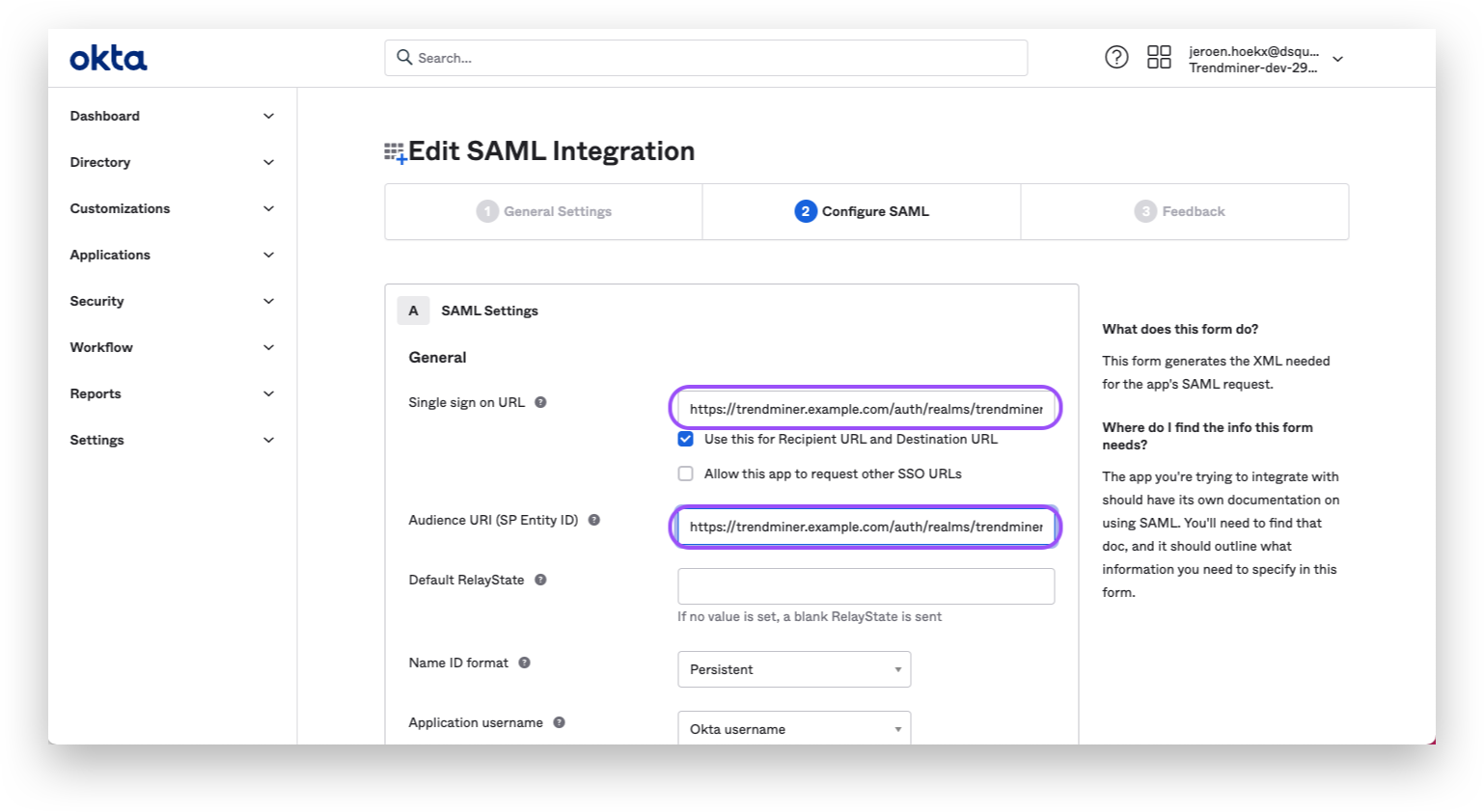
Copy the Location value from <md:SingleLogoutService>. In this example this corresponds to: https://trendminer.example.com/auth/realms/trendminer/broker/7fc6524e-3d55-4ae2-9edf-3d678e376063/endpoint. This URL needs to be added in OKTA.
Navigate in Okta to your application and open the "General"-tab.
Click "edit" for the SAML settings and proceed to step 2 "Configure SAML".
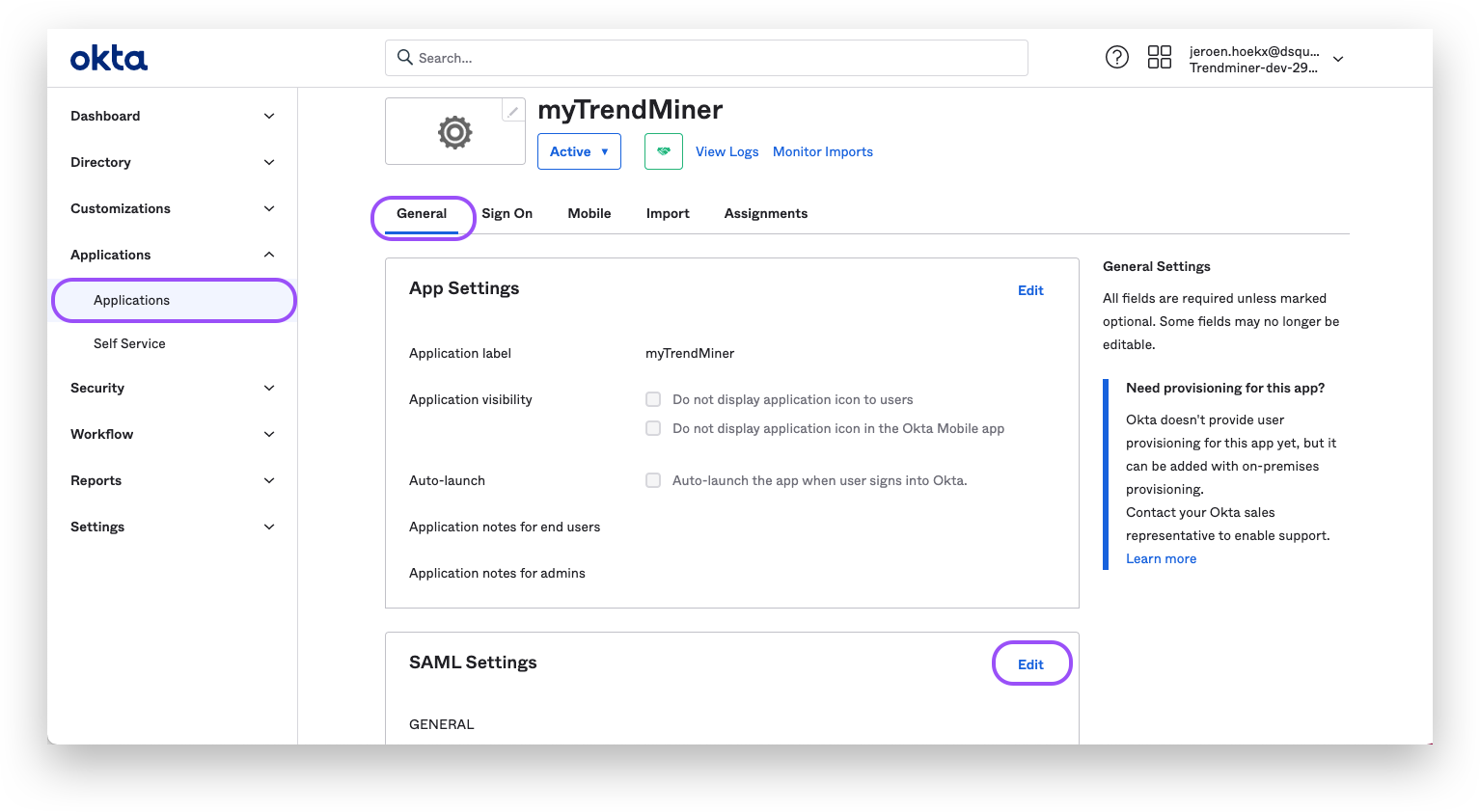
Change the "Single sign on URL" and "Audience URI" to the copied URL.
The SAML setup is complete and you should be able to login in TrendMiner. After logging in with a SAML user in TrendMiner the assigned groups should be synced and ACLs can be configured.