SSL
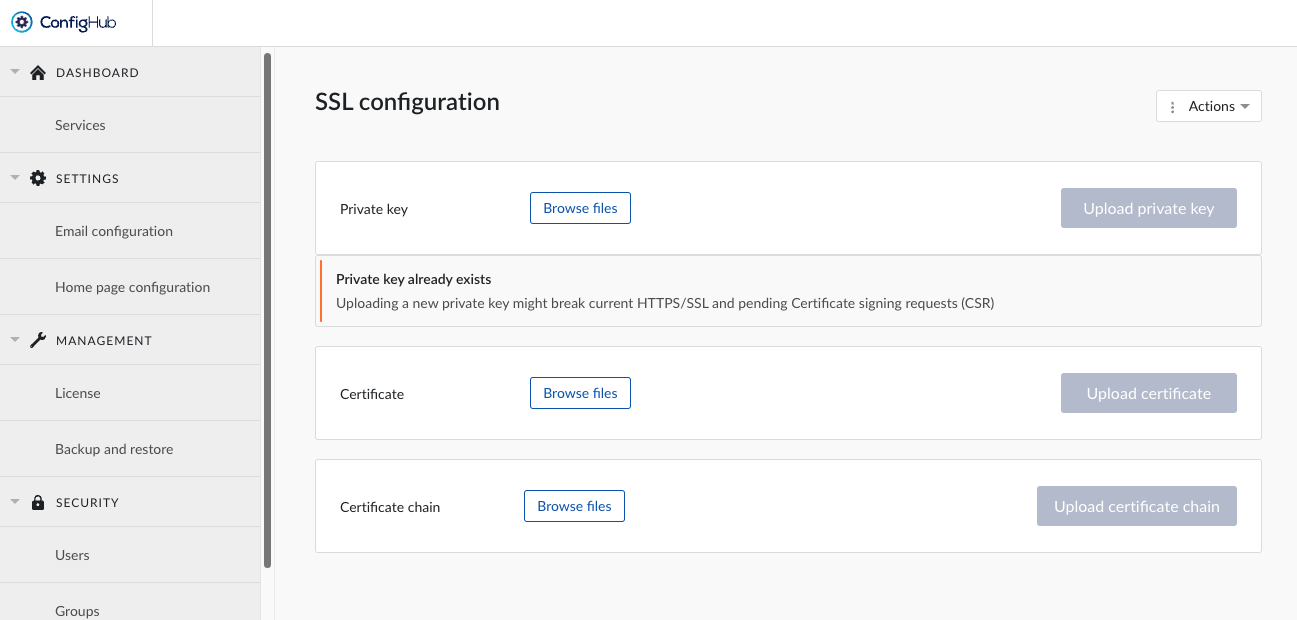
To enable HTTPS, three things are required:
Private key
CSR for that private key
Certificate chain
TrendMiner only supports PEM certificates. OpenSSL can be used to convert certificates in a different format to PEM.
Once these prerequisites are fulfilled, HTTPS can be enabled via the "Action" menu on the top right.
Note
Enabling HTTPS will temporarily render ConfigHub unusable until the service restart has completed. A manual refresh of ConfigHub is necessary. Press F5 to try to load the interface again. Retry until this succeeds.
Note
Certificate chain: If the certificate is issued directly by the root CA, upload the root CA, otherwise upload the intermediate CA which signed the certificate.
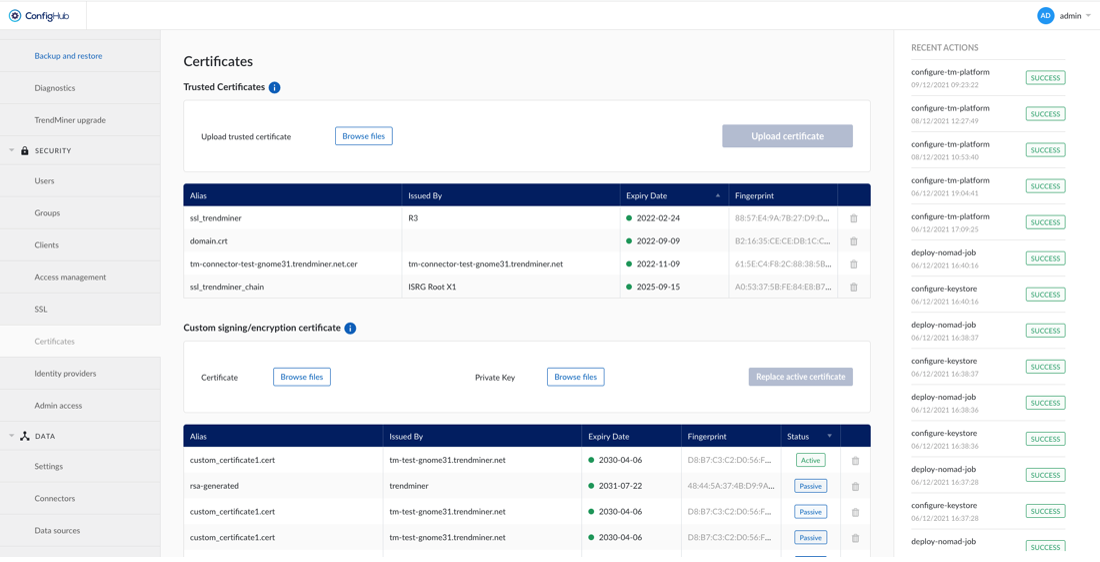
When uploading new trusted certificates via Security - Certificates and HTTPS is enabled, SSL can be reloaded by selecting “Reload SSL” in the Actions menu of the screen.
For a more detailed guide of what is, why and how to use SSL in TrendMiner, please consult our support documents.
Certificate signing request (CSR)
Via ConfigHub a CSR can be generated.
To start, clicking the Actions menu and select “Certificate signing request”. A side panel will open to download or generate the CSR.
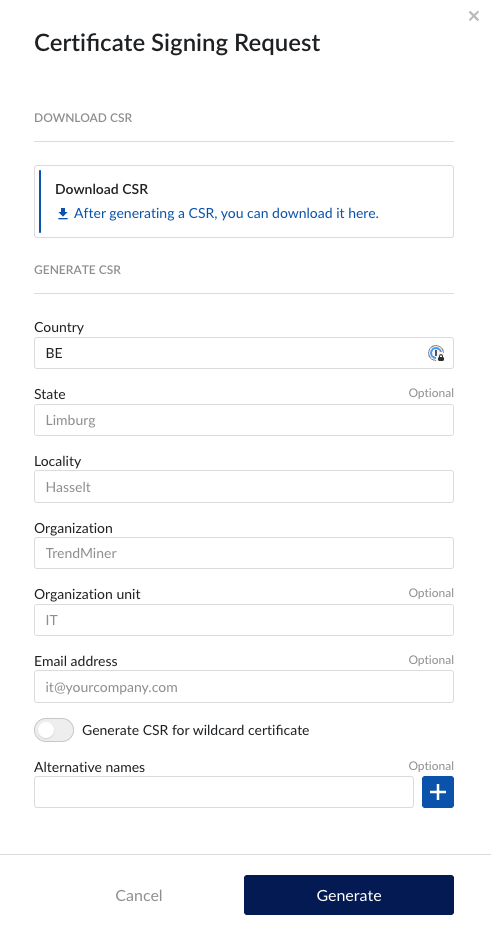
At the top of the side panel, you can download the CSR when it is generated on the server.
Below this section, information to generate the CSR can be provided. There are 2 options to generate a CSR, using
Alternative names
With this option, it is allowed to provide alternative fully qualified domain names to be protected using the certificate. These are optional. However, the server name of the installation must be listed as well as an alternative name.
Wildcard
This options allow for HTTPS on all subdomains of the provided wildcard domain. This domain is required.
When no private key is available yet, one will be generated. Uploading a new private key, might break current HTTPS/SSL and pending Certificate signing requests (CSR).
If TrendMiner needs to communicate with SSL enabled services (Plant Integrations, LDAP, ...) that are using self signed certificates or certificates issued by an internal CA, it's not possible to verify the trust chain of these certificates.
To be able to verify the trust chain please upload the root CA and optionally one or multiple intermediate CA certificates. The same is needed when using SAML with certificates issued by an internal CA.