Where to get your private key?
Note
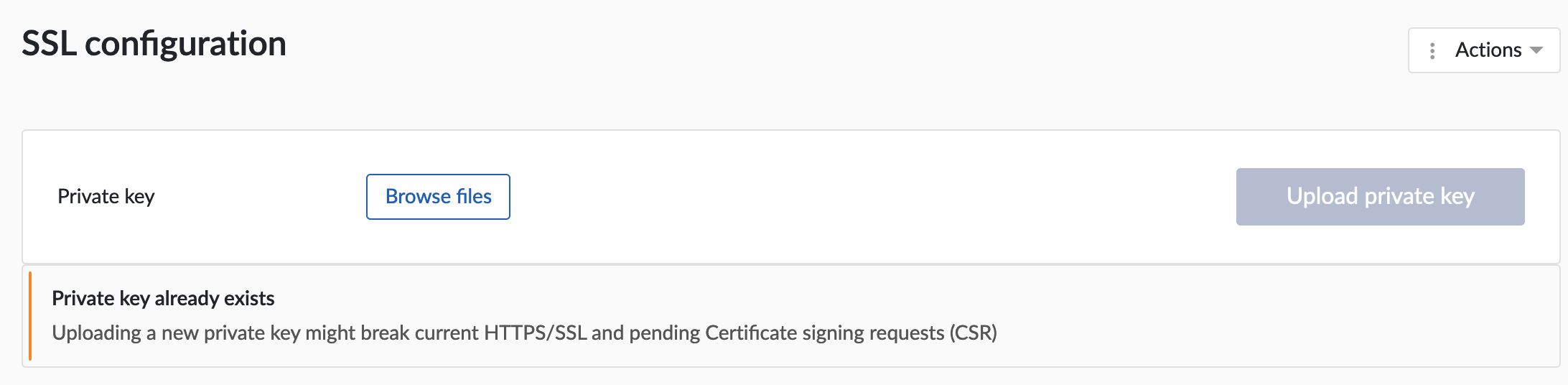
When a CSR was generated via ConfigHub the private key is already available on the server and no new private key has to be uploaded together with the certificates. This is indicated with the message "Uploading a new private key might break current HTTPS/SSL and pending Certificate signing requests (CSR)" in the ConfigHub UI.
When you request a certificate the CA (certificate authority) will generate a certificate and a private key. The certificate and the private key can be sent over in a single file (e.g. a .pfx file) or as a separate files.
To enable SSL the private key needs to be uploaded separately so in case a single pfx file is received a manual action is required to extract the private key from the pfx file.
With openssl the following command can be used to extract the private key from the pfx file:
openssl pkcs12 -in filename.pfx -nodes -nocerts -out private.key
The "-nodes" (no DES) option prevents the private key from being encrypted. This is essential as TrendMiner does not support uploading an encrypted private key.
The "-nocerts" option makes sure no certificates are in the output file and only the private key will be output.
Note
Since the pfx file contains the private key it is passphrase protected and you will be prompted to enter the passphrase when executing the command. You should have received the passphrase from your IT department or CA.
Alternatively you can convert the pfx file to a pem file first and then extract the private key with the following command:
openssl x509 -in filename.pem -nocerts -out private.key
As a third option you can convert the pfx file to a pem file first and then extract the private by manually copying it:
Open the .pem file with a text editor
Copy everything between "-----BEGIN PRIVATE KEY-----" and "-----END PRIVATE KEY-----", including these 2 lines
Save the copied text to a new text file and save it as a .key file
How to decrypt your private key?
As mentioned above an encrypted private key is not supported in TrendMiner. You can open your private.key file with any text editor and verify if the contents start with: "-----BEGIN ENCRYPTED PRIVATE KEY-----"
This means that the private key is encrypted. The following openssl command can be used to decrypt the private key file based on the provided passphrase:
openssl rsa -in encrypted.key -out decrypted_private.key
When you open the decrypted_private.key file the content should start with: "-----BEGIN PRIVATE KEY-----"