Setting up SAML with Azure AD
SAML - Configure Entra (Azure AD)
Steps to do in this first part of the guide
Create the enterprise application in Entra
Setup SSO
Configure placeholders for security claims
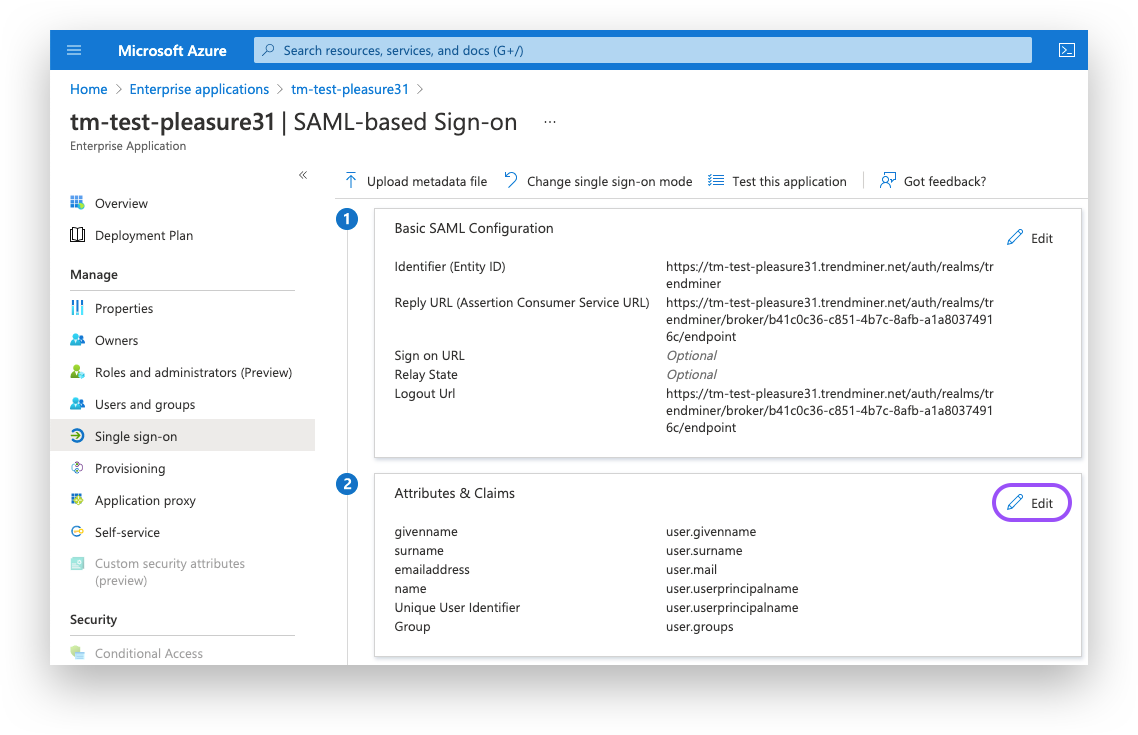
Configure Attributes & Claims
Add users and groups to your application
Download the Federations metadata XML from Entra
1. Create the enterprise application in Entra
Browse to https://entra.microsoft.com and login with a administrator account that is having access to create new Enterprise applications and SAML configuration
Go to Applications→Enterprise applications
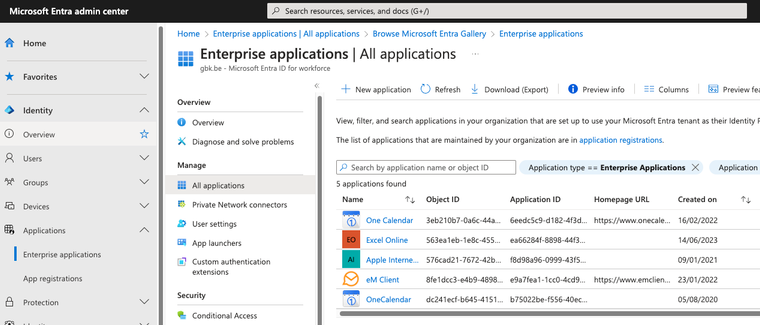
Click ‘New Application’ and then click on ‘Create your own Application’
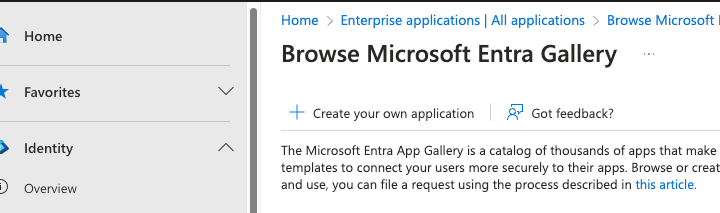
Fill in the name of the application and select ‘Integrate any other application you don’t find in the gallery'
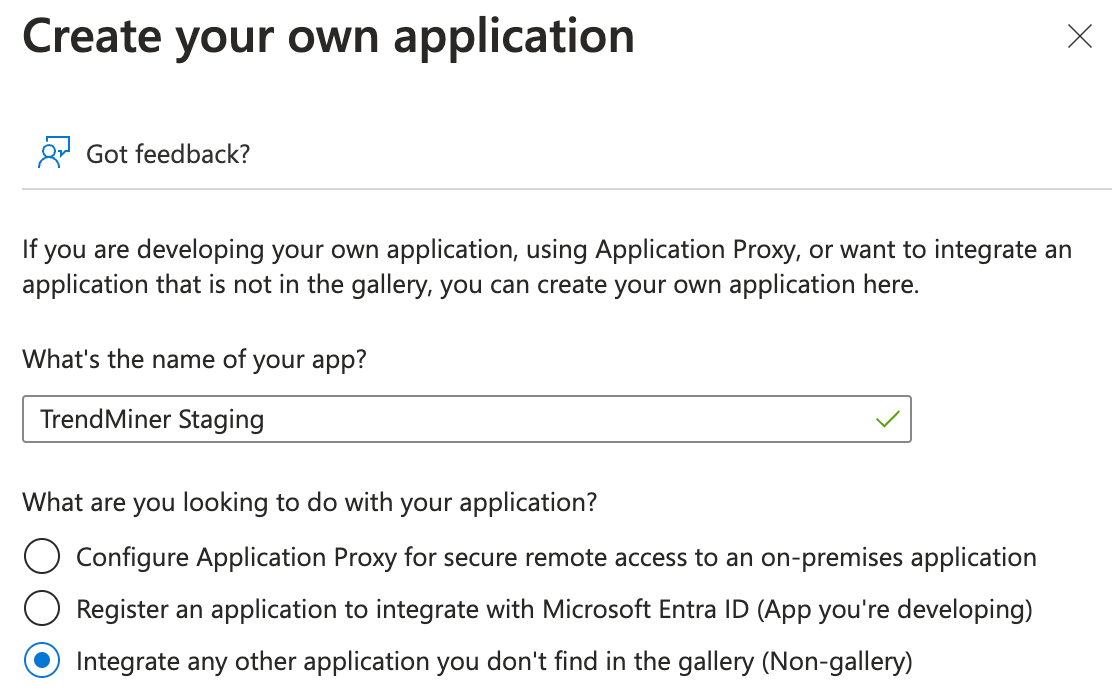 |
Click on Create
2. Setup SSO
Click on “Single sign-on”
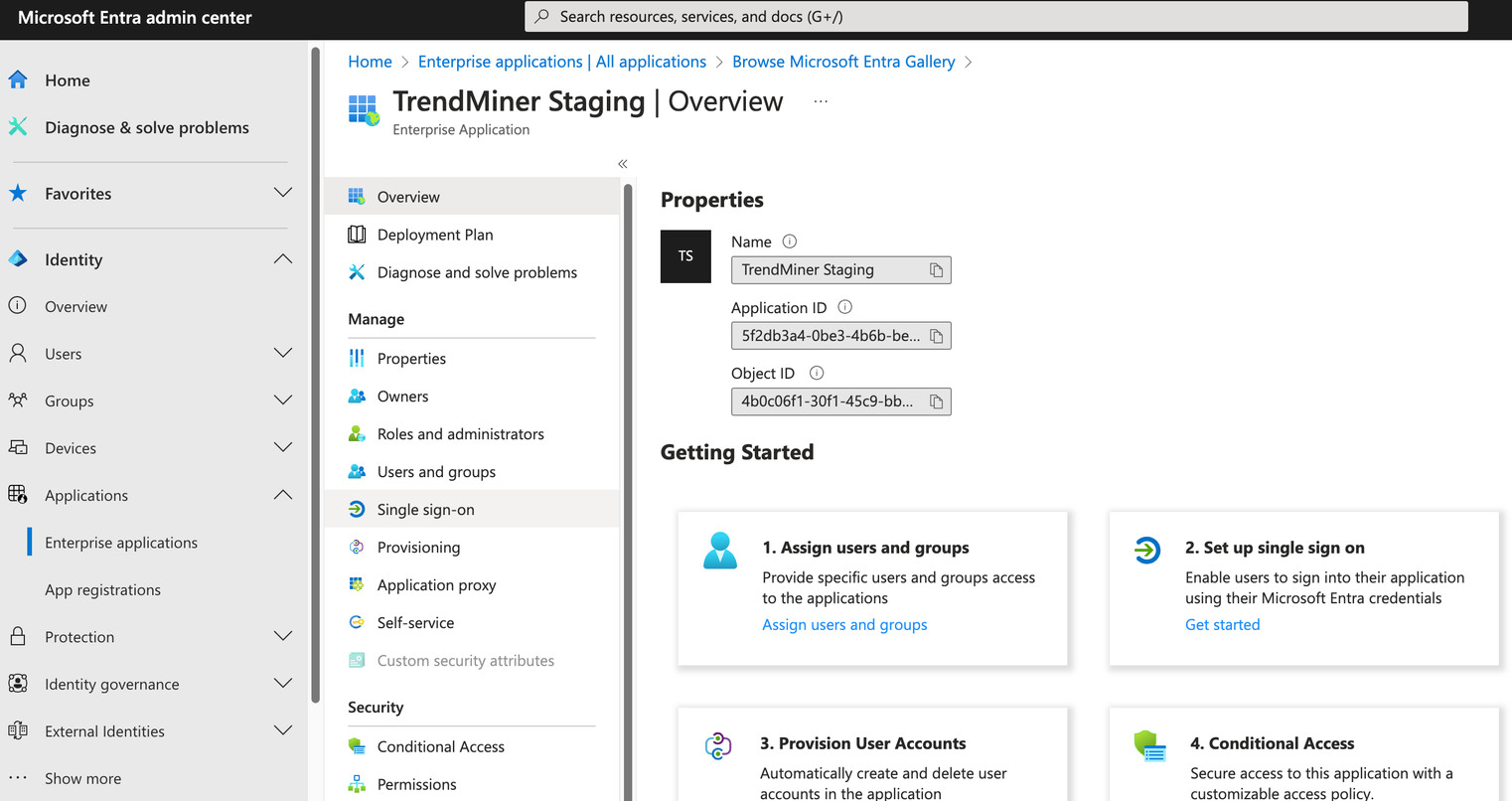
Then Click on SAML
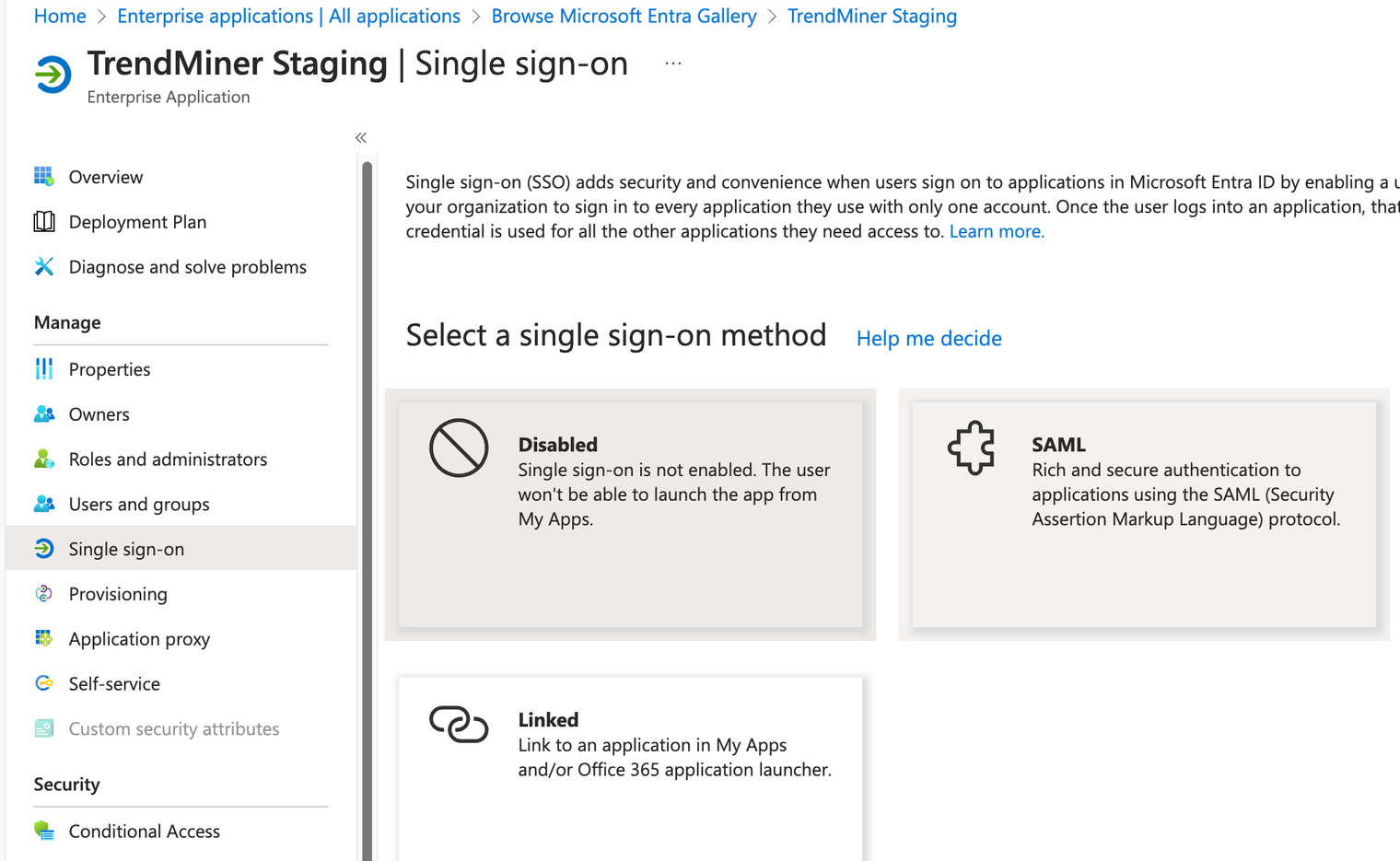
3. Configure placeholders for security claims
Identifier (Entity ID) and Reply URL
This step is required to be able to download “Federation Metadata XML” needed to setup TrendMiner
Click on edit
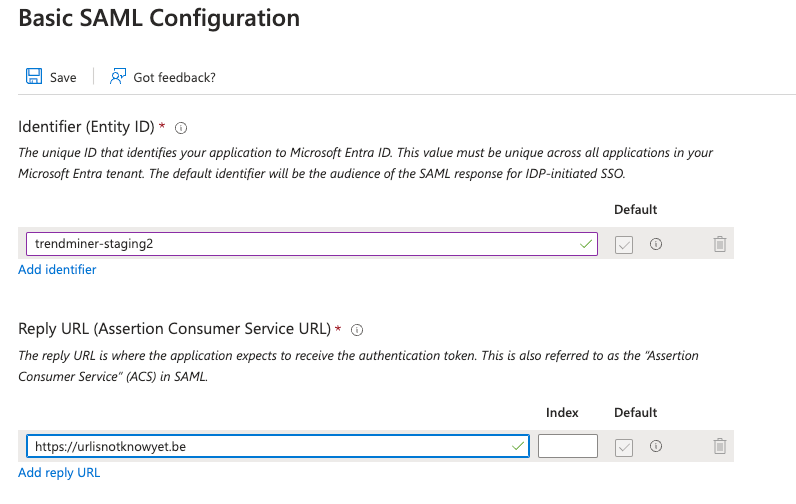
Fill in the parameters as below.
Identifier (Entity ID): Fill in some name, this is only used temporary and will be replaced.
Reply URL: currently not yet known, will be automatically fixed in the further steps.
4. Configure Attributes & Claims
Configure user attributes & claims. This enables the automatic creation of user profiles, including the user name they will be identified with in TrendMiner.
Click the "Edit"-button under "User Attributes & Claims"
Click on the "Unique User Identifier (Name ID)" option.
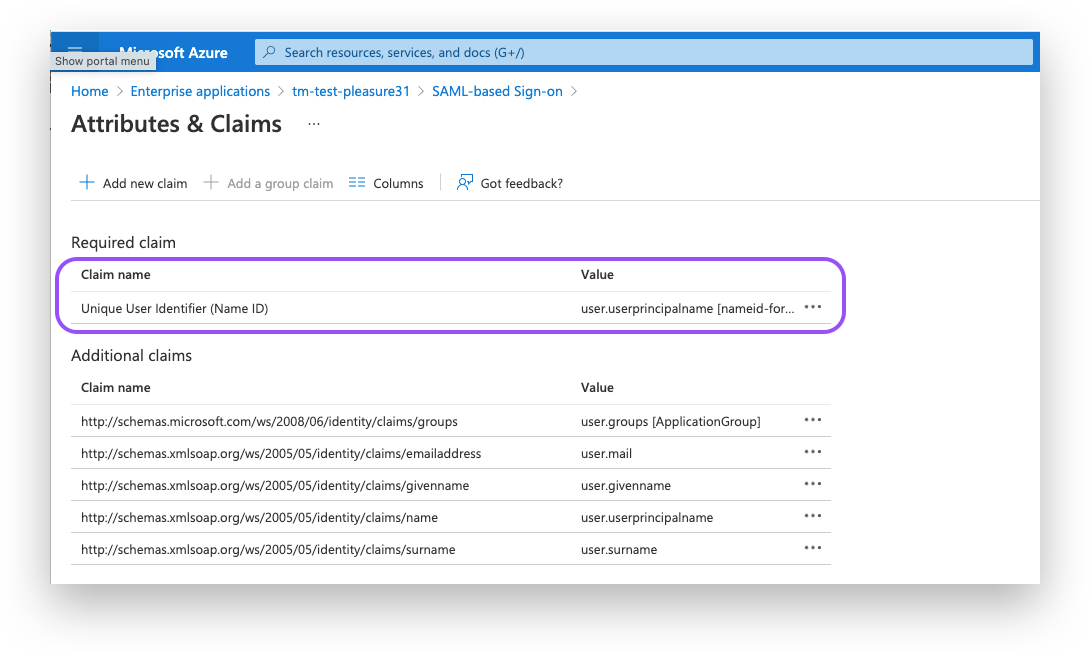
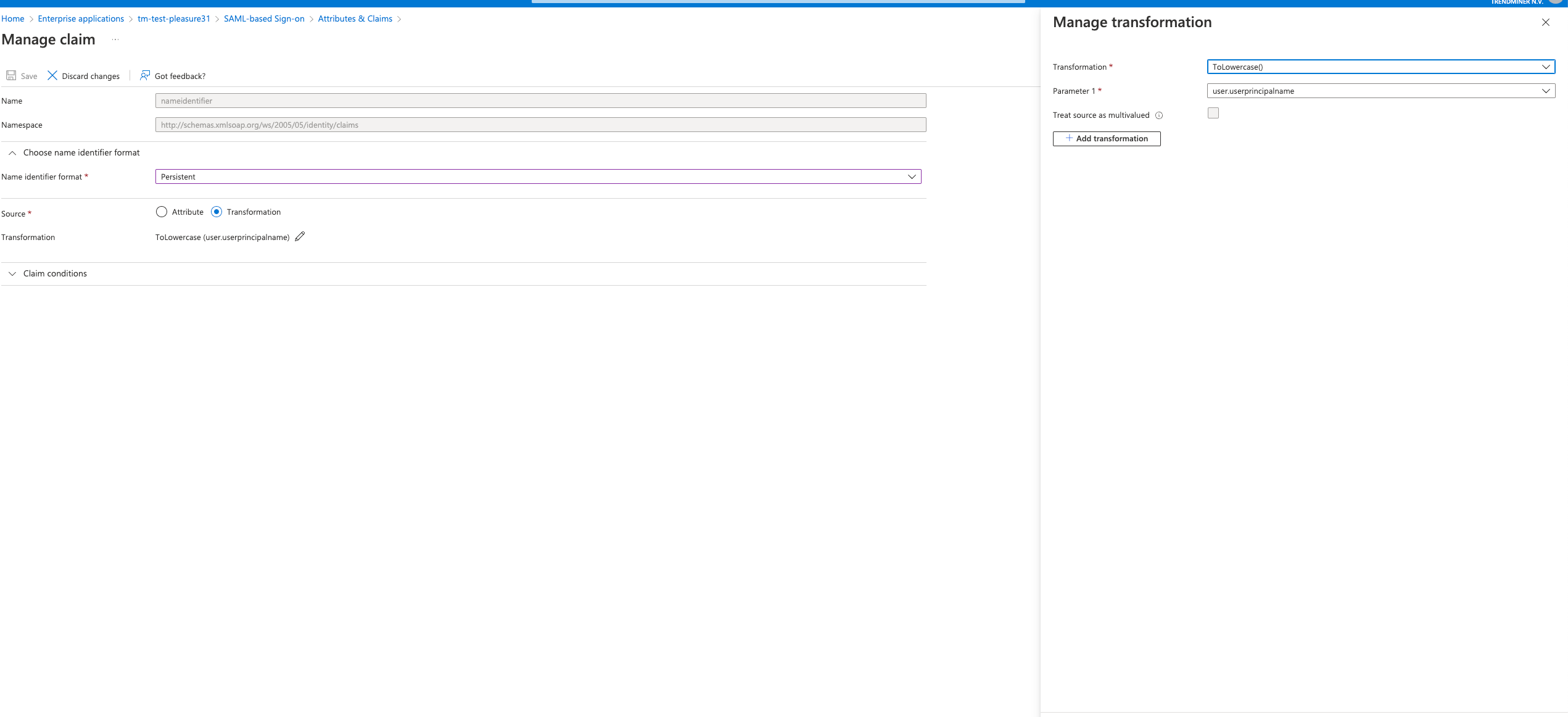
Ensure the “Name identifier format” is set to a format of your choice. Note that the source attribute "user.userprincipalname" refers to the email in Azure. Under "Source" select ''Transformation" and add the "ToLowercase()" transformation for the "user.userprincipalname" as shown in the screenshot below.
Configure groups. This helps you leverage existing group memberships to set access rights to data sources automatically.
Click the "Edit"-button under "User Attributes & Claims"
Click the "Add a group claim"-option.
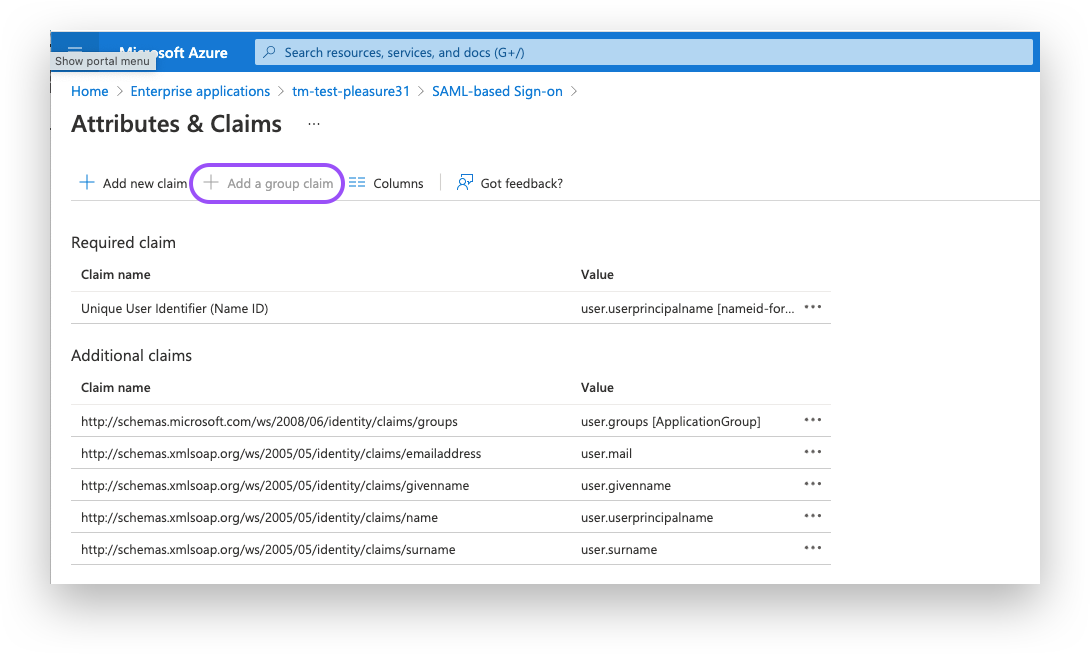
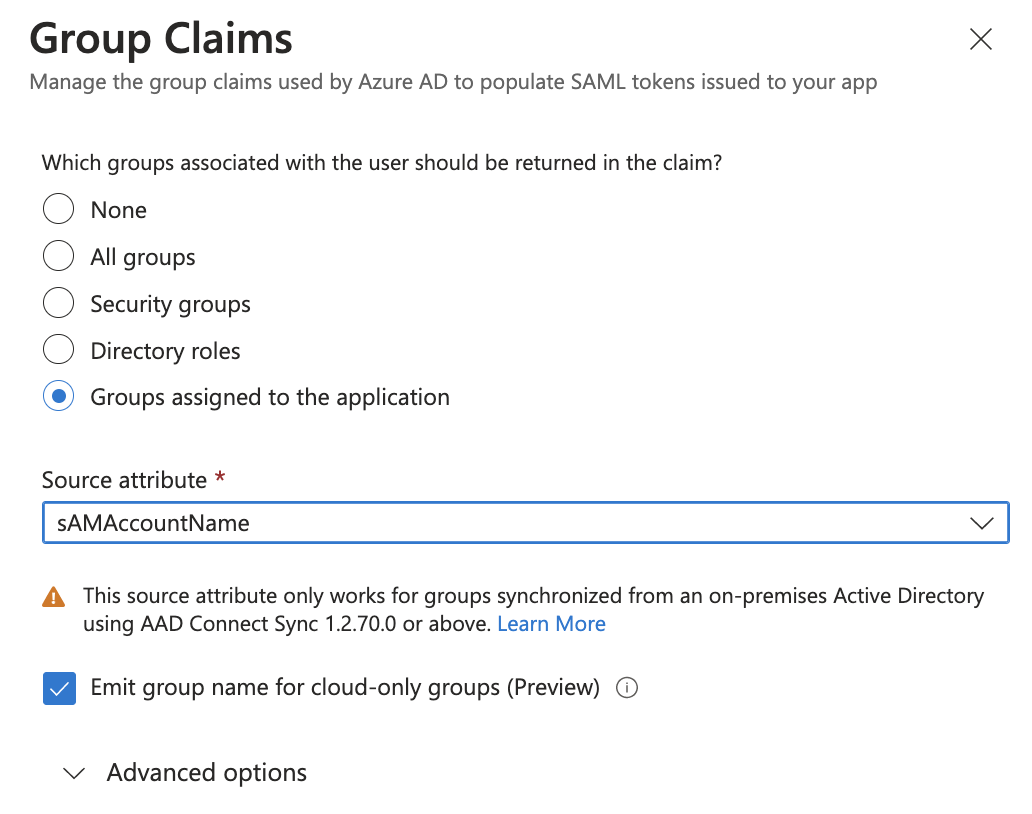
Set the Group Claims as desired. An example is shown in the screenshot below; this needs to be adjusted to fit your preferences:
Associated groups to be returned in the claim: to avoid clutter, the recommendation is to select "Groups assigned to the application".
Source attribute: Select your preference according to the Azure AD documentation. In most cases, either sAMAccountName (for groups that are synchronized from an on-premise Active Directory setup into Azure AD) or Group names for cloud-only groups (for groups that were created directly in Azure AD) will be desired, as these return human-readable names that can be used in TrendMiner's ConfigHub.
Caution
By default, the Group ID will be selected as Source Attribute. This corresponds to the Object ID of the Azure AD group, typically a 37-character string in the format xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx. The group will be identified in Confighub as this long identifier as well, so for human readability and admin usability, it is recommended to change the Source attribute.
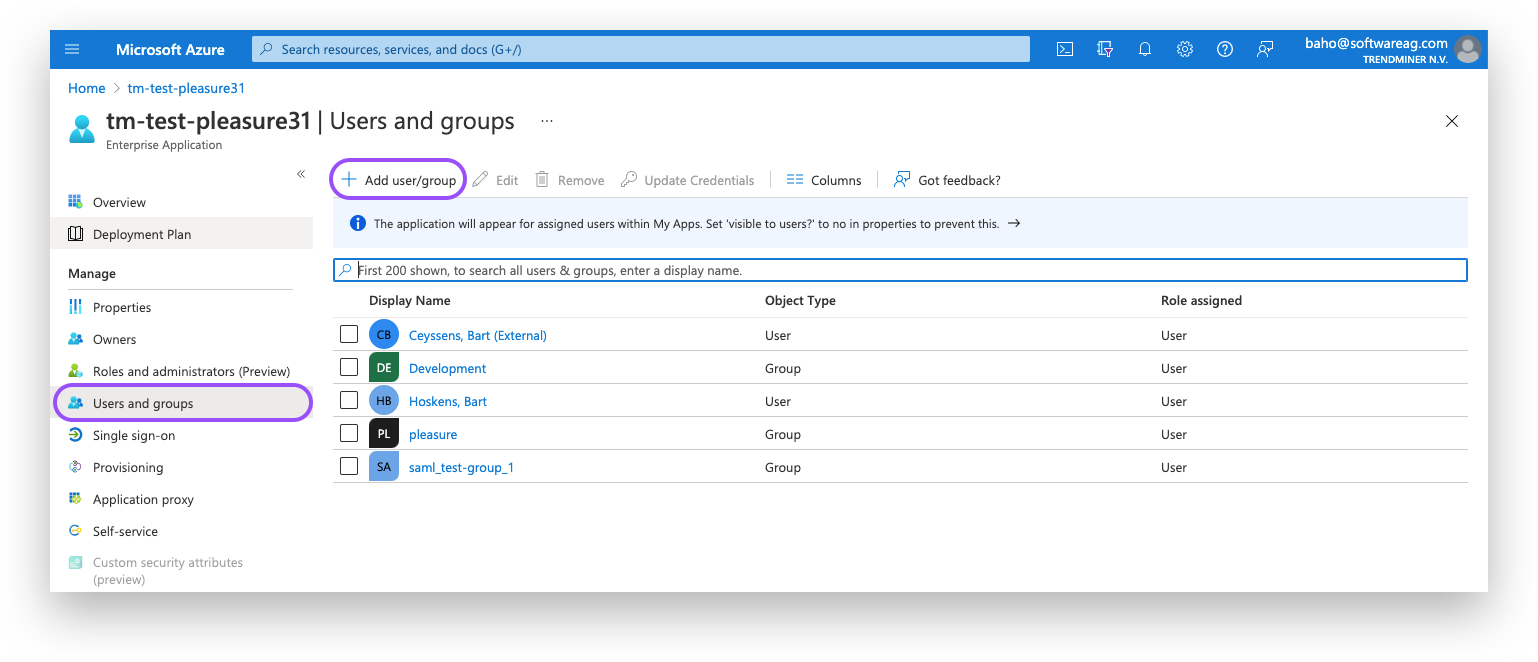
5. Add users and groups to your application
Add users/groups to the application. This enables the admin to provide explicit access only to those users and groups that should be able to use TrendMiner, according to the provisioned license capacity for named users.
Navigate to "the Users and Groups" tab.
Click the Add "user/group" button and add users/groups.
6. Download the Federations metadata XML from Entra
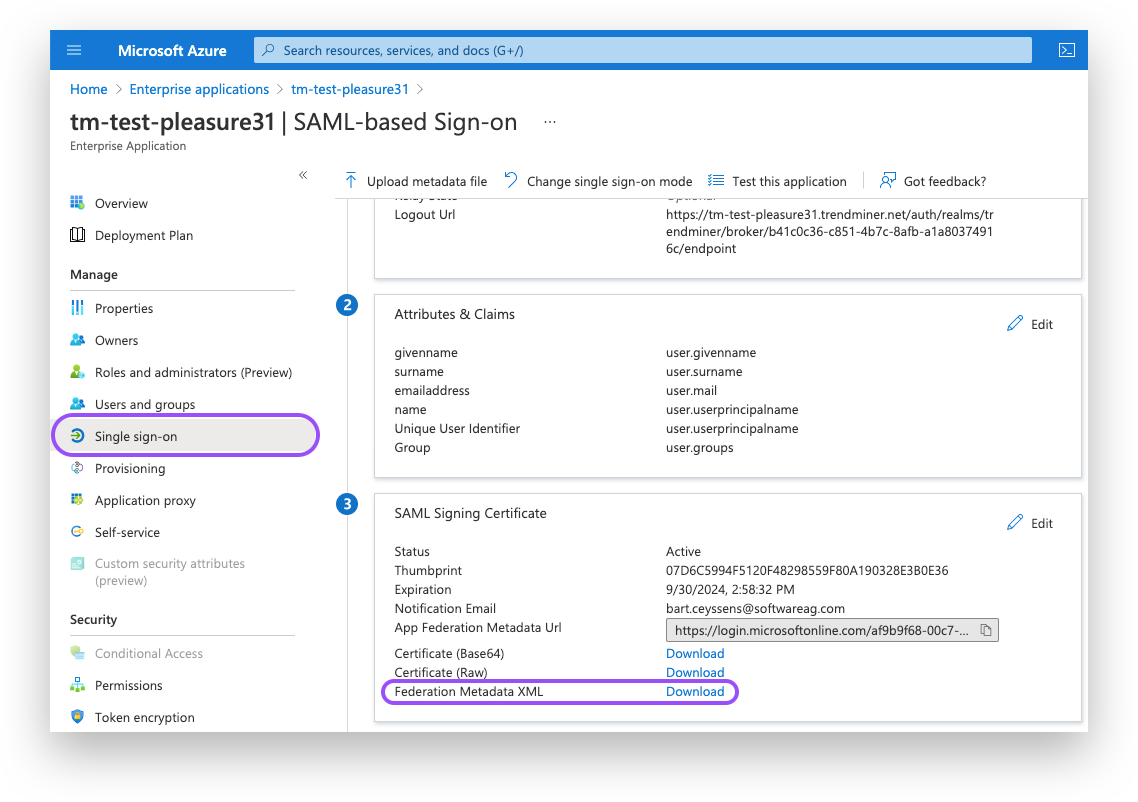
Navigate in Entra ID to your SAML application, and open the Single Sign-on section.
1. In the upper section, "Basic SAML Configuration", leave placeholders for the required fields like Entity ID. These values will be overwritten in later steps when the metadata file from TrendMiner is imported back into Azure AD.
2. Download the Federation Metadata XML. This file will be used to upload in TrendMiner ConfigHub in later steps.
Continue with the steps for TrendMiners ConfigHub configuration as explained in the next section of this document.
SAML - ConfigHub Configuration
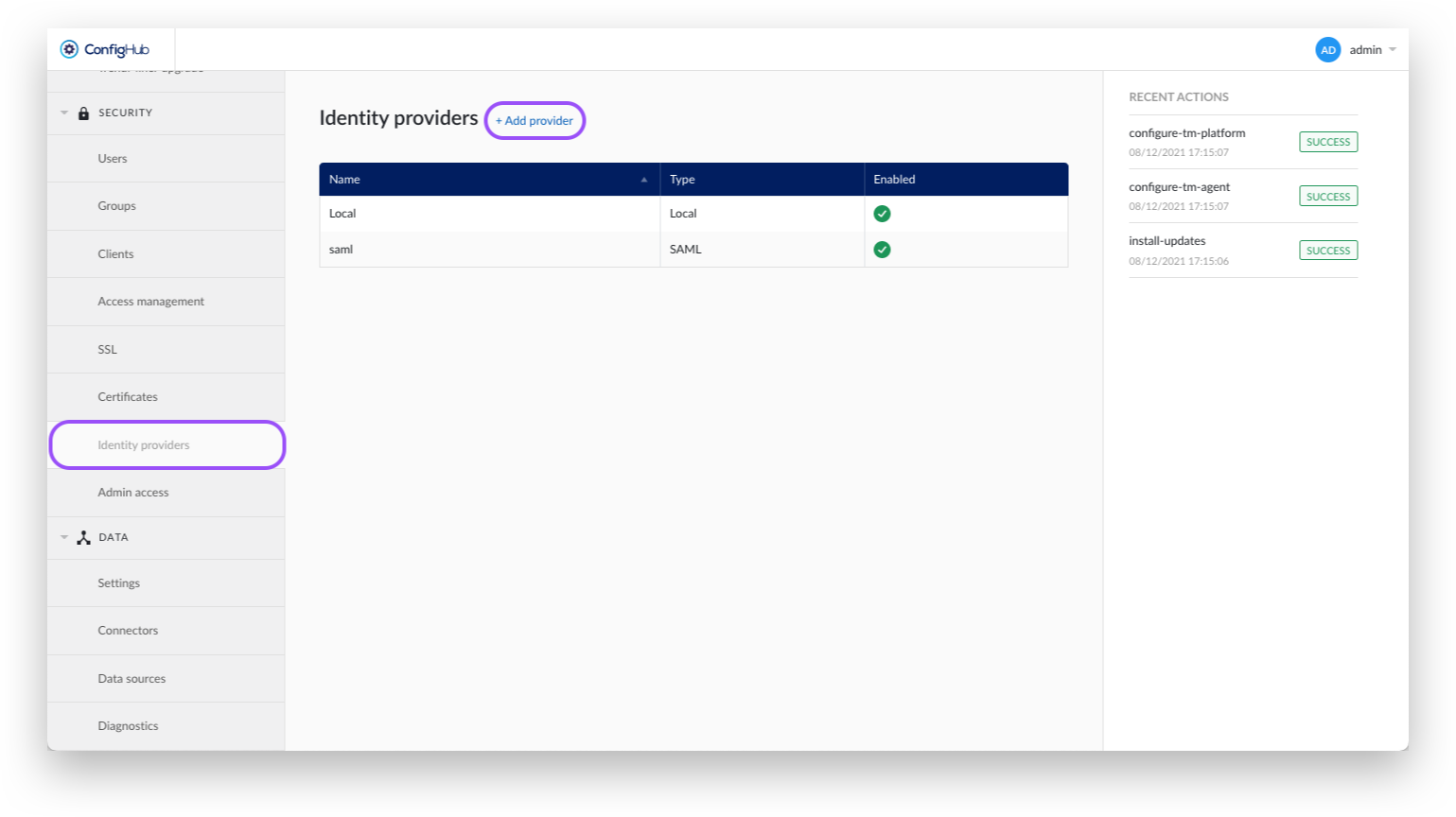
After setting up the initial application in your Identity Provider, we can continue in TrendMiner's ConfigHub. Via ConfigHub we can see an overview of the existing Identity Providers and have the ability to configure a new one.
Navigate to ConfigHub and open the "Identity Providers" tab in the "Security" section.
Click the "Add provider"-button.
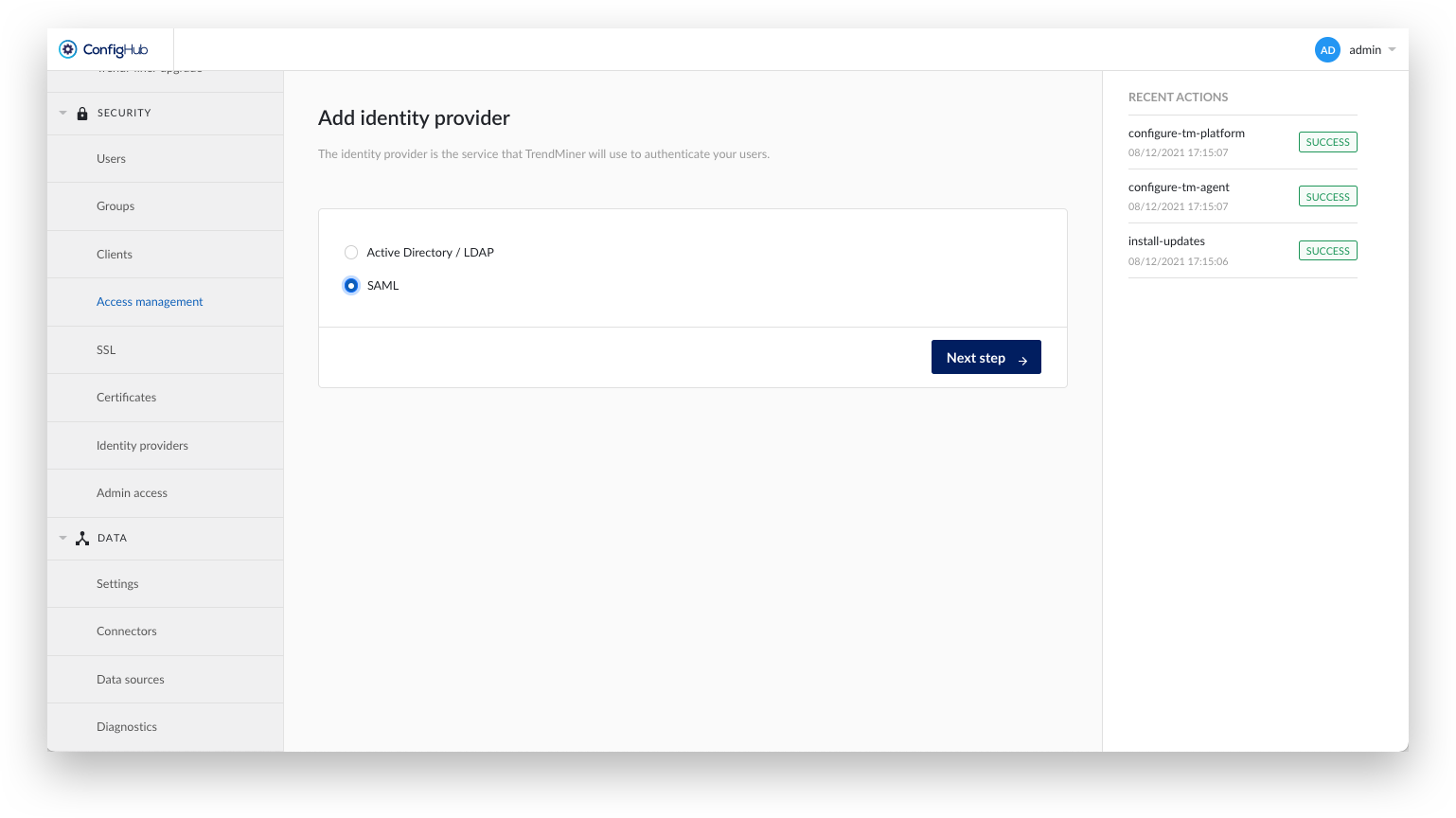
Select the SAML option.
Create a TrendMiner backup.
Upload a Self-signed certificate if necessary. Self-signed certificates might be necessary if the IDP uses a custom CA certificate over HTTPS.
Indicate whether a signed Assertion is expected.
Fill out the details for the SAML configuration:
Name: Display name in ConfigHub and used as root group. This name is only used within ConfigHub for admins to recognize the configuration. It does not further relate to any technical SAML details.
Base domain: Used in URLs of the SP metadata file. Eg: where the IDP has to redirect after identification.
NameID Policy Format: A dropdown to select the policy format as being used by the SAML provider (e.g. Azure or Okta). Possible values are: Persistent, Transient, Email, Kerberos, X.509 Subject Name, Windows Domain Qualified Name, Unspecified
Principal Type: A dropdown to select the principal type as being used by the SAML provider. Possible values are: Subject name ID, Attribute name, Attribute friendly name
Principal Attribute: In case Attribute name or Attribute friendly name was selected as an option from the Principal Type dropdown, an extra input field will become visible that allows you to enter the name of the specific attribute to be used
Identity provider metadata file: Upload the Federation Metadata XML file you have downloaded from the IdP in the previous section.
Enable Attributes Mapping: Optional setting to map SAML assertions into ConfigHub. Note that the mappings need to correspond with the attribute names used from the IdP (see previous section).
For Azure, this corresponds to the claim name, e.g.
First name: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname
Last name: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/surname
E-mail: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
Group: http://schemas.microsoft.com/ws/2008/06/identity/claims/groups
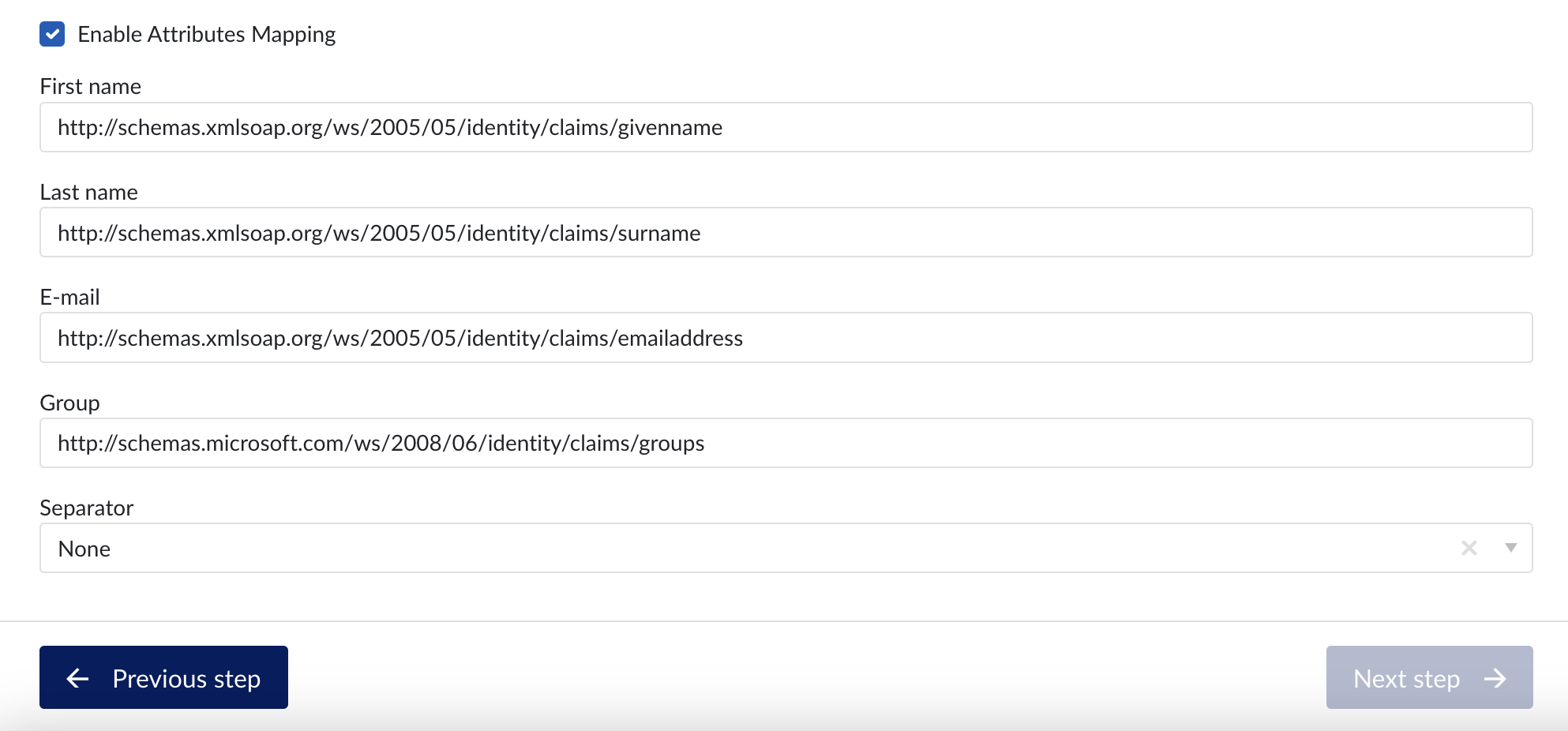
For Okta this corresponds to the given names in the previous steps (e.g. firstName, groups,…).
The next screen allows mapping existing (local) TrendMiner users to the SAML provider. The SAML username should correspond to the value returned by the IdP in the Subject-NameID tags. TrendMiner requests the NameId in the following format:
"urn:oasis:names:tc:SAML:2.0:nameid-format:persistent".
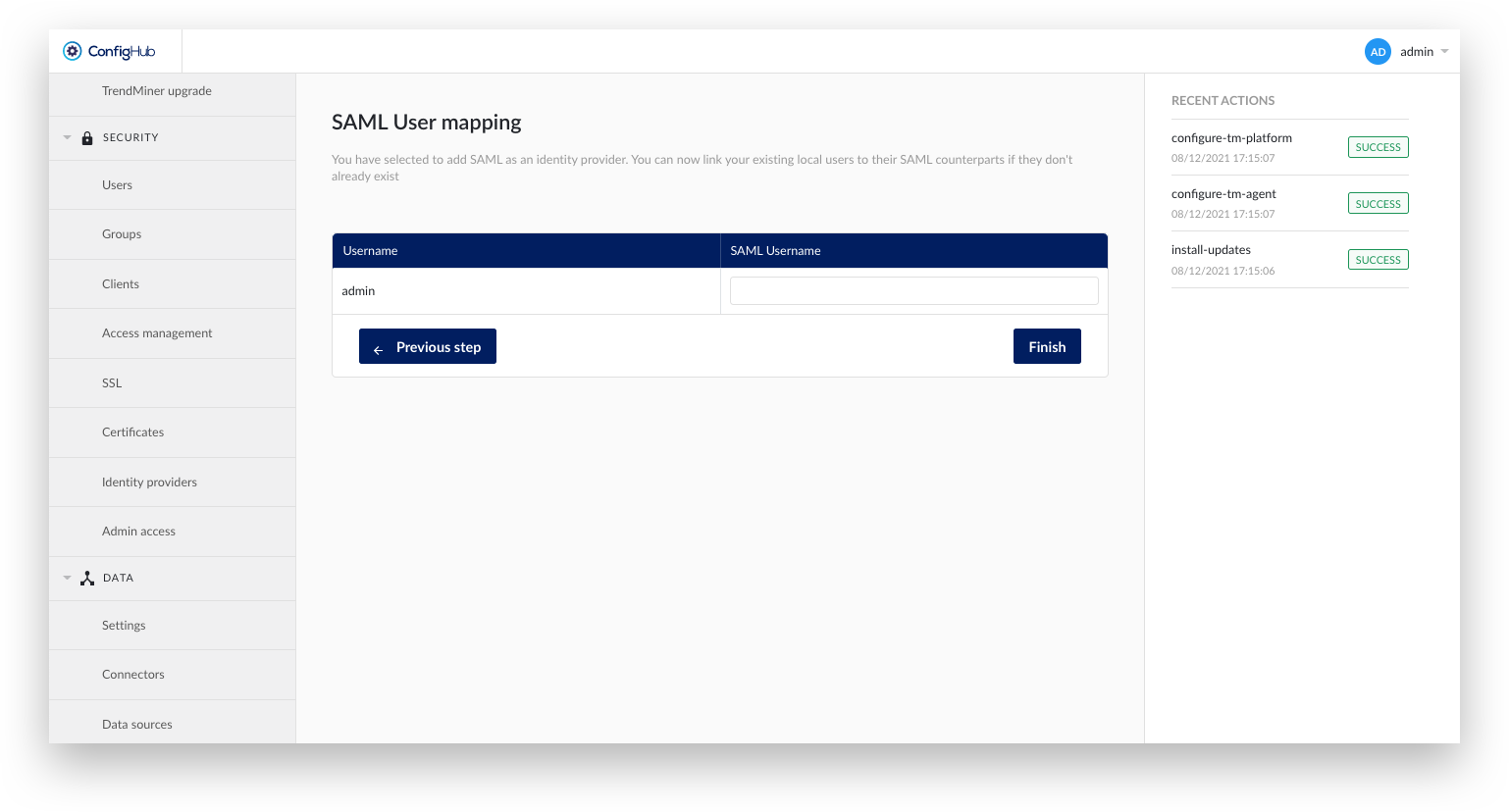
After creating the identity provider in ConfigHub it is time to download the metadata file and go back to the identity provider.
Go back to the "Identity Providers" tab in the "Security" section in ConfigHub. You should be able to see your created provider listed.
Click on your newly created provider. A side panel will pop open.
Click the options-button.
Click the download Metadata button. This metadata file contains the remaining configuration on the IdP side.
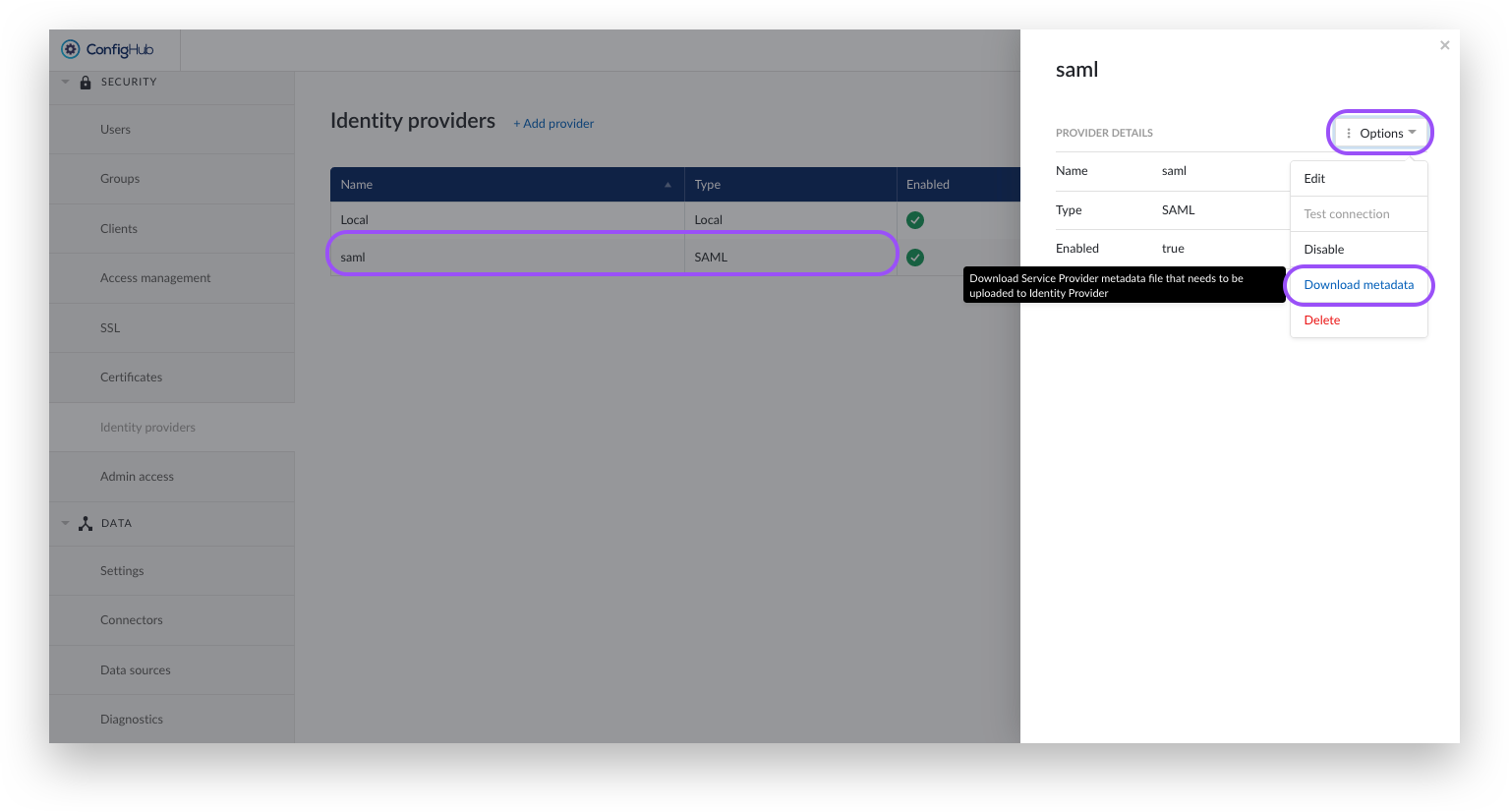
Complete the identity provider configuration as explained in the next section.
SAML - Configure Azure AD - Part 2
Now that we have the metadata file from TrendMiner (as generated in the previous step), we can proceed with finalizing the configuration on the IdP side.
Navigate in Azure AD to your SAML application and open the "Single sign-on"-tab.
Click the "Upload metadata file" and upload the TrendMiner metadata file. This will fill out the required information where we placed placeholders in the first step.
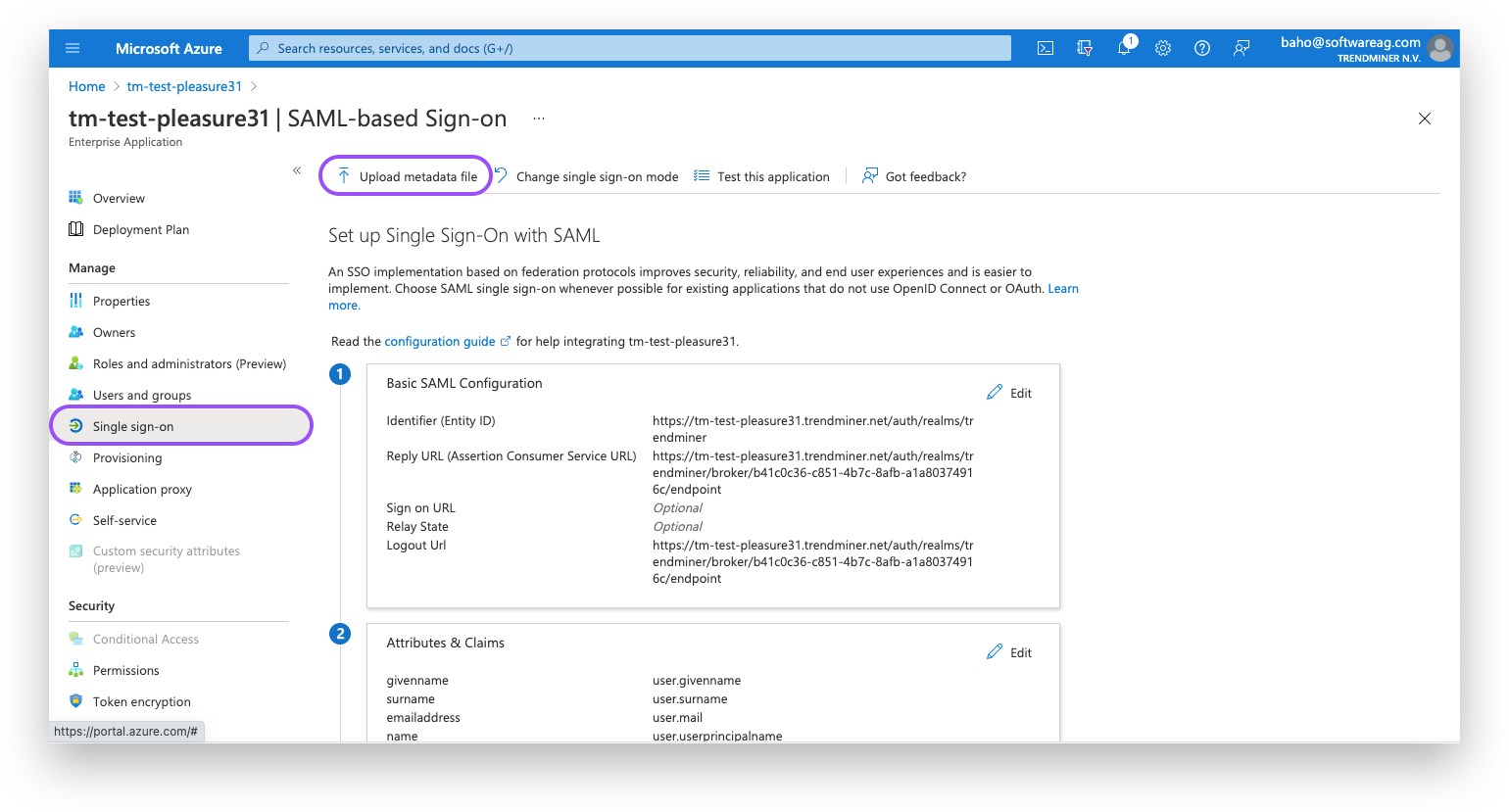
Check the entries - It might be necessary to fill in the Reply URL yourself. This is the same value as Logout URL.
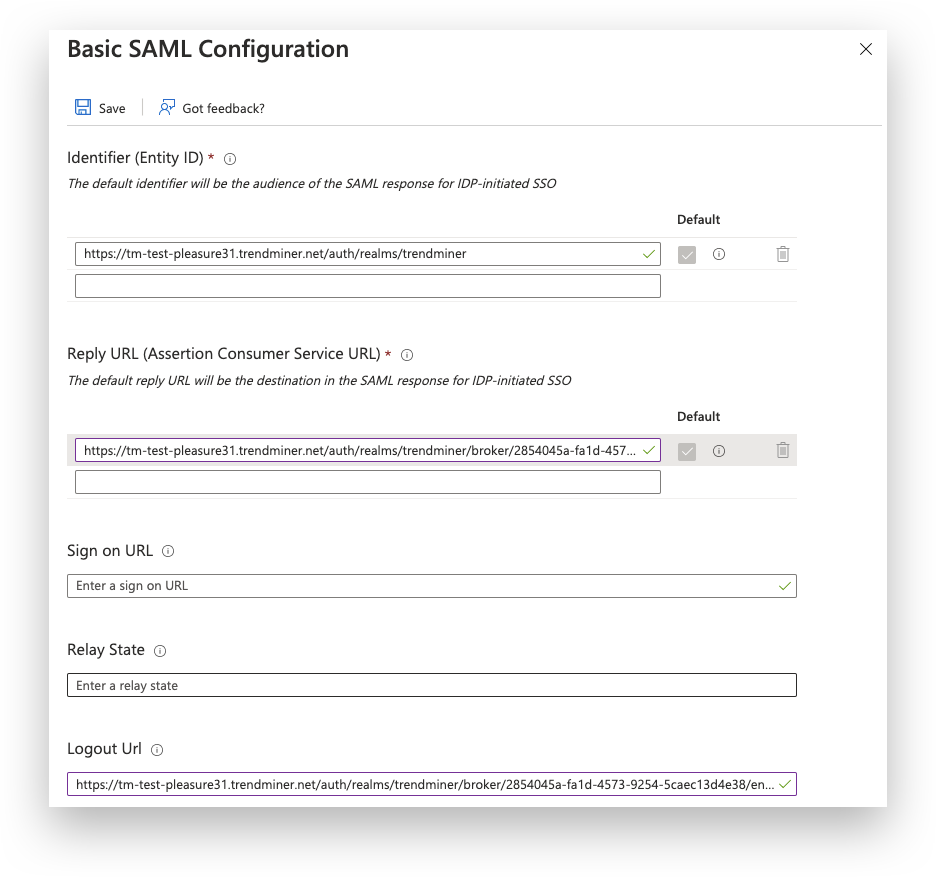
The SAML setup is complete and you should be able to login in TrendMiner. After logging in with a SAML user in TrendMiner the assigned groups should be synced and ACLs can be configured.